2025/2026 WGU MASTER'S COURSE C726 - CYBERSECURITY ARCHITECTURE AND ENGINEERING
Course:
WGU MASTERS COURSE
Institution:
WGU MASTERS COURSE
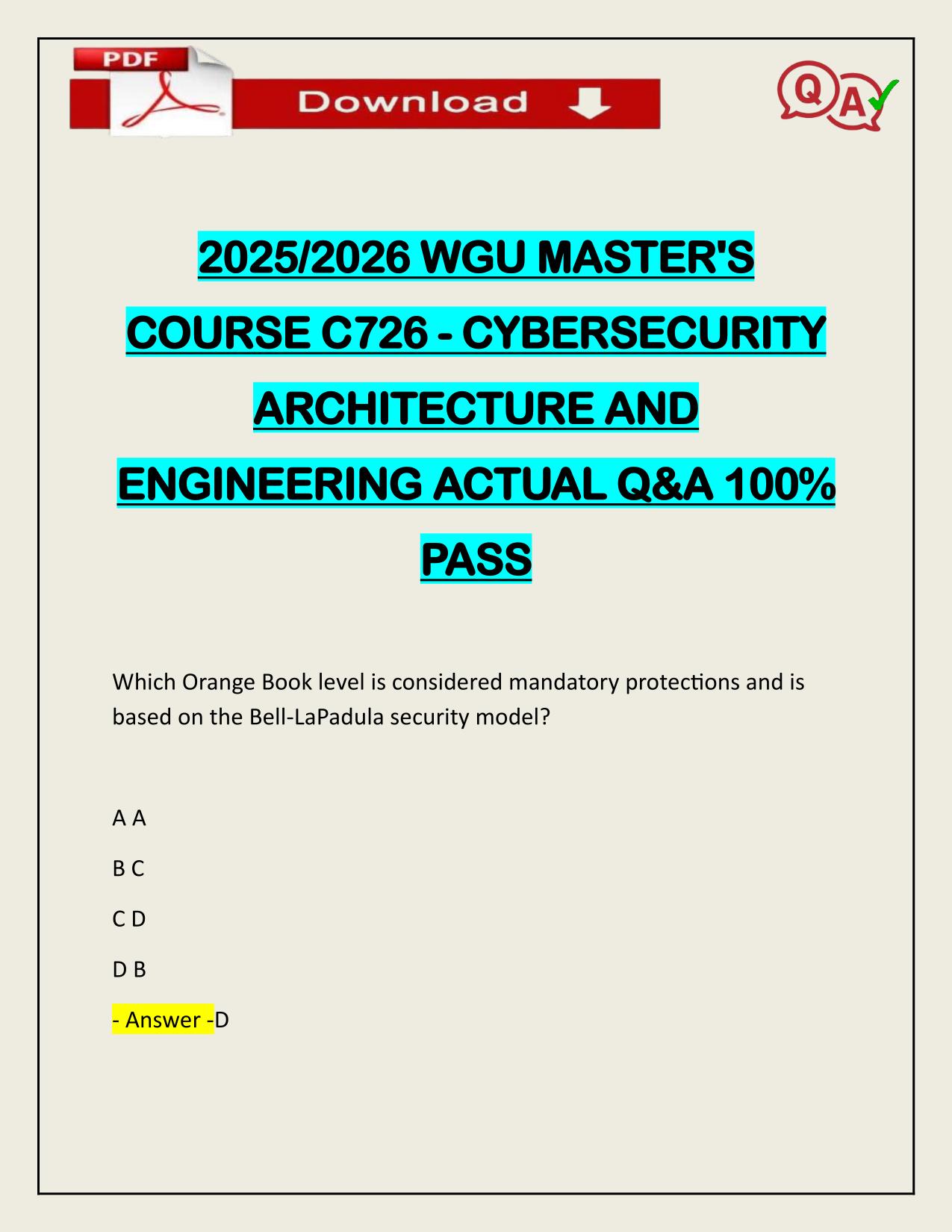
2025/2026 WGU MASTER'S COURSE C726 - CYBERSECURITY ARCHITECTURE AND ENGINEERING ACTUAL Q&A 100% PASS Which Orange Book level is considered mandatory protections and is based on the Bell-LaPadula security model? A A B C C D D B - Answer -D
After purchase, you get:
✅ Instant PDF Download
✅ Verified answer explanations
✅ Refund if not Satisfied
✅ Prepared for 2025/2026 test cycle
Overview
The document uses a clear, methodical approach to help learners build exam habits rooted in strong reasoning. You're developing systematic problem-solving routines that become automatic with practice. These habits help you work more efficiently and reduce decision fatigue during lengthy exams. Many test-takers find these methodical approaches make them feel more organized and in control during high-pressure testing situations. Each section in 2025/2026 WGU learn thoroughly'S COURSE C726 - CYBERSECURITY ARCHITECTURE AND ENGINEERING is tailored to build exam certainty through progressively challenging items and clear solutions. The material starts with foundational concepts and gradually introduces more complex applications. This scaffolding approach means you're always working at the edge of your abilities without feeling overwhelmed. Many learners appreciate how this progressive challenge keeps them engaged and motivated throughout their preparation.
Who Is This For?
A helpful guide for individuals needing organized repetition and progressive question difficulty tied to / WGU become proficient in'S COURSE C726 - CYBERSECURITY ARCHITECTURE AND ENGINEERING learning goals. Many users appreciate how it gradually increases challenge levels. The building-block approach supports sustainable learning progress.
Related Keywords
Detailed Study Description
Frequently Asked Questions
Document Information
| Uploaded on: | October 27, 2025 |
| Last updated: | November 17, 2025 |
| Number of pages: | 46 |
| Written in: | 2025/2026 |
| Type: | Exam (elaborations) |
| Contains: | Questions & Answers |
| Tags: | 2025/2026 WGU MASTER'S COURSE C726 - CYBERSECURITY ARCHITECTURE AND ENGINEERING ACTUAL Q&A 100% PASS Which Orange Book level is considered mandatory protections and is based on the Bell-LaPadula security model? A A B C C D D B - Answer -D |
Seller Information

AdelineJean
User Reviews (0)
Exam (Elaborations)
$11.00
Bundle Deal! Get all 7 docs for just $24.00
Add to Cart
100% satisfaction guarantee
Refund Upon dissatisfaction
Immediately available after purchase
Available in Both online and PDF
$11.00
| 0 sold
Discover More resources
Available in a Bundle
Inside The Document
2025/2026 WGU MASTER'S COURSE C726 - CYBERSECURITY ARCHITECTURE AND ENGINEERING ACTUAL Q&A 100% PASS Which Orange Book level is considered mandatory protections and is based on the Bell-LaPadula security model? AA BC CD DB - Answer -D During an XOR operation, two bits are combined. Both values are the same. What will be the result of this combination? A1 B0 C OR DX - Answer -B Which section of the Minimum Security Requirements for Multi-User Operating System (NISTIR 5153) document addresses end-to-end user accountability? A access control B audit C data integrity Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com D system integrity - Answer -B Which encryption algorithm is based on the Diffie-Hellman key agreement? A Knapsack B International Data Encryption Algorithm C El Gamal D HAVAL - Answer -C What is meant by the term fail-safe? A system's ability to switch over to a backup system in the event of a failure B system's ability to preserve a secure state before and after failure C system's ability to recover automatically through a reboot D system's ability to terminate processes when a failure is identified - Answer -D You need to store some magnetic storage devices in a temporary storage facility. At which temperature could damage start to occur? A 350 degrees Fahrenheit B 100 degrees Fahrenheit C 90 degrees Fahrenheit D 175 degrees Fahrenheit - Answer -B You need to decrypt a file that is encrypted using asymmetric encryption. What should be used to decrypt the file? A public key Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com
CourseHero & Studypool Unlocks
Get Unlocked CourseHero and Studypool documents files instantly to your email, simply by pasting your link and clicking "Unlock Now". Learn more on how to unlock here.