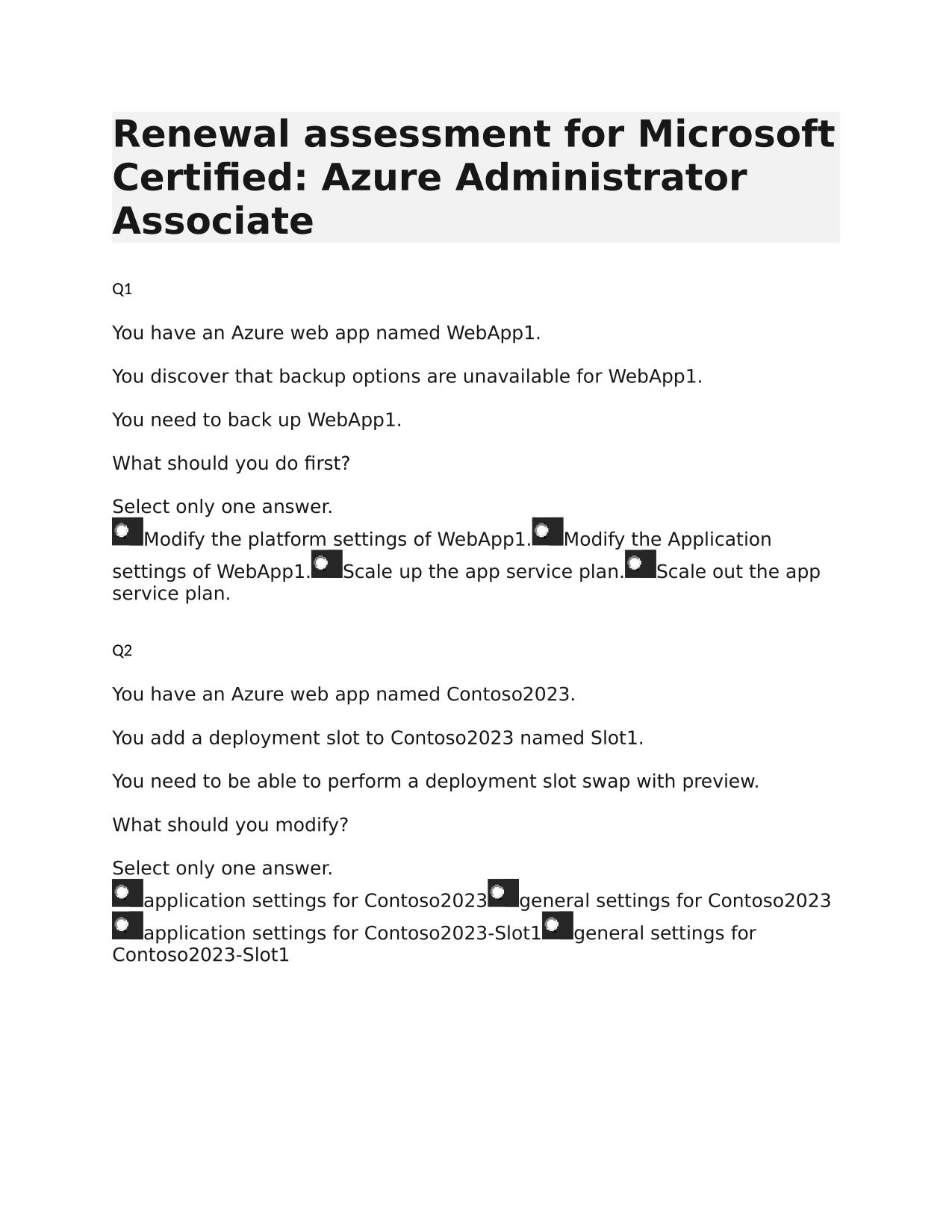
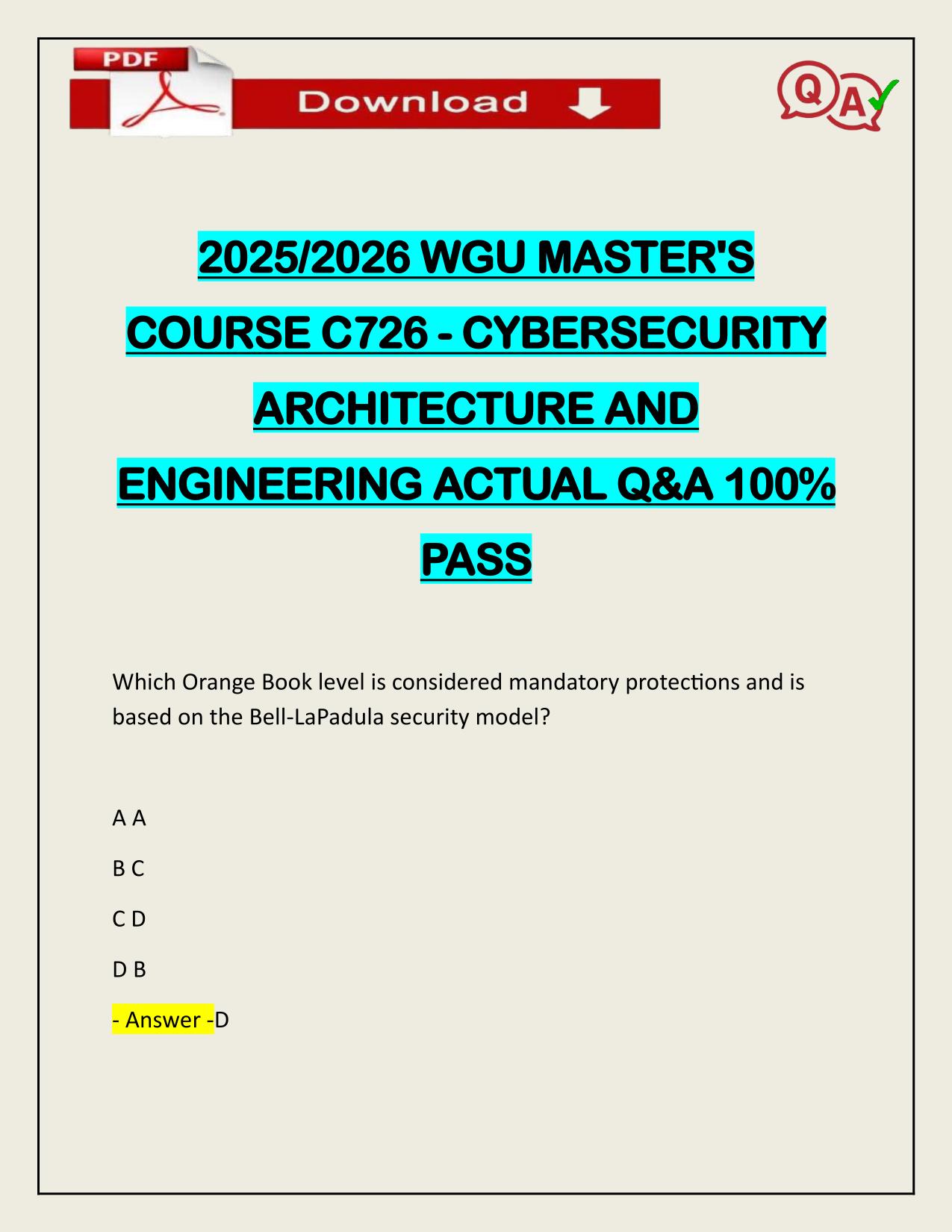
2025/2026 WGU MASTER'S COURSE C701 - ETHICAL HACKING (PRACTICE EXAM 124Q)
Course:
WGU MASTERS COURSE
Institution:
WGU MASTERS COURSE
2025/2026 WGU MASTER'S COURSE C701 - ETHICAL HACKING (PRACTICE EXAM 124Q) ACTUAL Q&A 100% PASS Which of the following information security elements guarantees that the sender of a message cannot later deny having sent the message and the recipient ca...
After purchase, you get:
✅ Instant PDF Download
✅ Verified answer explanations
✅ Refund if not Satisfied
✅ Prepared for 2025/2026 test cycle
Overview
Topic clustering helps learners stay organized and review related questions together for maximum retention. Grouping similar concepts makes it easier to see connections and understand how ideas interrelate. This organized approach is particularly helpful during final review sessions when you need to refresh multiple related topics quickly. Many students find they remember information better when it's presented in meaningful clusters rather than isolation.
Who Is This For?
A strong fit for learners in WGU MASTERS COURSE looking to develop exam familiarity, question interpretation skills, and test-taking assurance. Students often share this resource with classmates during study groups. The practical approach has proven helpful across different learning styles.
Related Keywords
Detailed Study Description
Frequently Asked Questions
Document Information
| Uploaded on: | October 27, 2025 |
| Last updated: | November 17, 2025 |
| Number of pages: | 73 |
| Written in: | 2025/2026 |
| Type: | Exam (elaborations) |
| Contains: | Questions & Answers |
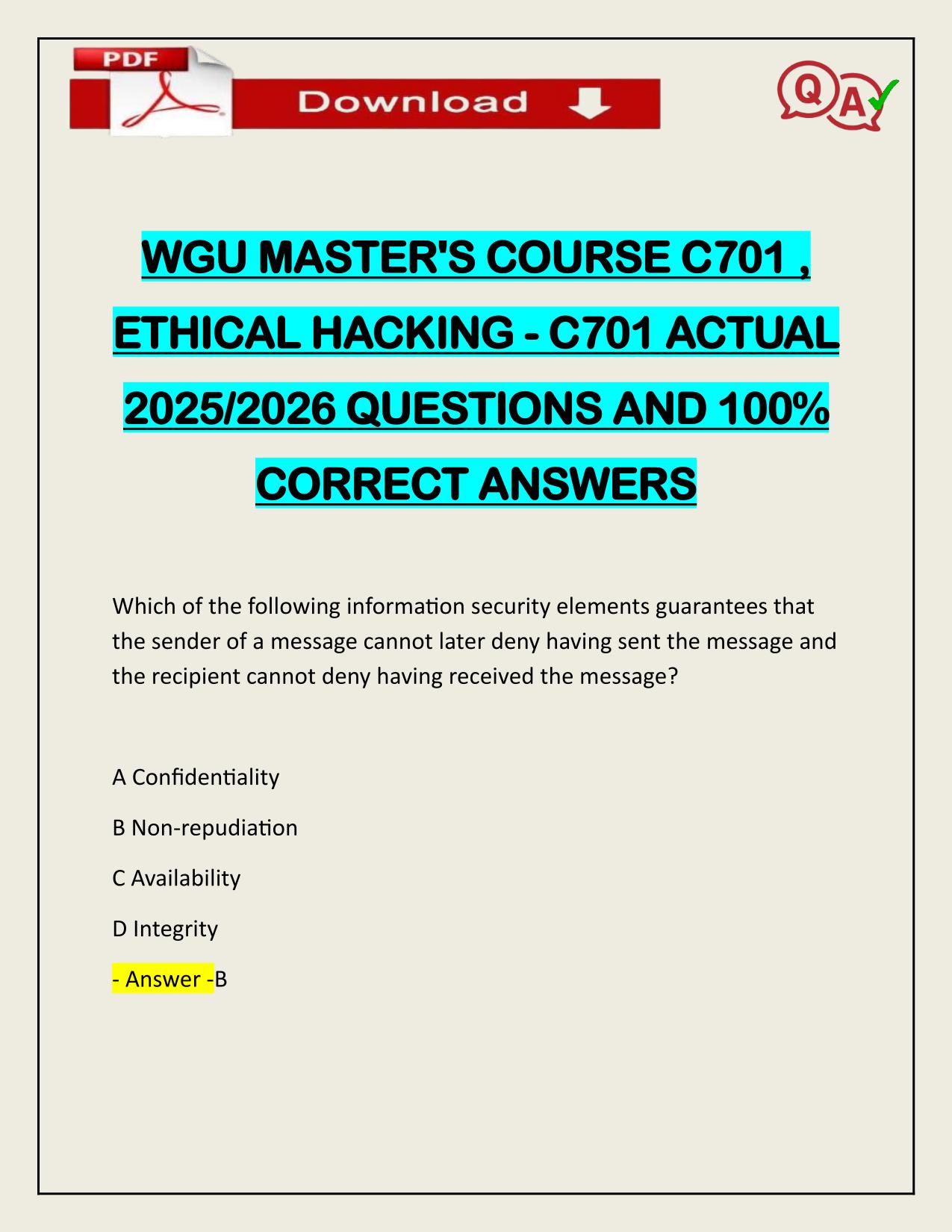
| Tags: | 2025/2026 WGU MASTER'S COURSE C701 - ETHICAL HACKING (PRACTICE EXAM 124Q) ACTUAL Q&A 100% PASS Which of the following information security elements guarantees that the sender of a message cannot later deny having sent the message and the recipient cannot deny having received the message? A Confidentiality B Non-repudiation C Availability D Integrity - Answer -B |
Seller Information

AdelineJean
User Reviews (0)
Exam (Elaborations)
$11.00
Bundle Deal! Get all 7 docs for just $24.00
Add to Cart
100% satisfaction guarantee
Refund Upon dissatisfaction
Immediately available after purchase
Available in Both online and PDF
$11.00
| 0 sold
Discover More resources
Available in a Bundle
Inside The Document
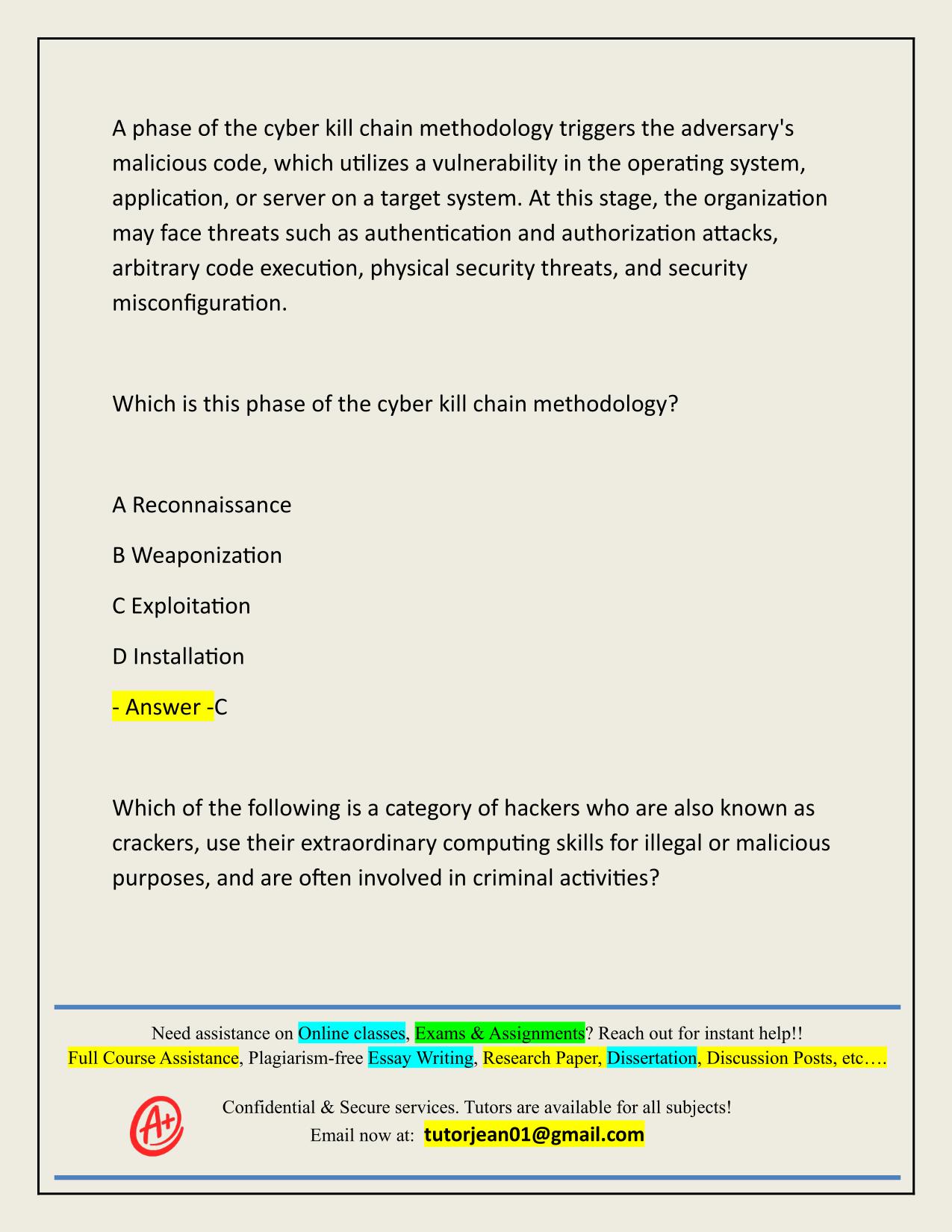
2025/2026 WGU MASTER'S COURSE C701 - ETHICAL HACKING (PRACTICE EXAM 124Q) ACTUAL Q&A 100% PASS Which of the following information security elements guarantees that the sender of a message cannot later deny having sent the message and the recipient cannot deny having received the message? A Confidentiality B Non-repudiation C Availability D Integrity - Answer -B A phase of the cyber kill chain methodology triggers the adversary's malicious code, which utilizes a vulnerability in the operating system, application, or server on a target system. At this stage, the organization may face threats such as authentication and authorization attacks, arbitrary code execution, physical security threats, and security misconfiguration. Which is this phase of the cyber kill chain methodology? A Reconnaissance B Weaponization C Exploitation D Installation - Answer -C Which of the following is a category of hackers who are also known as crackers, use their extraordinary computing skills for illegal or malicious purposes, and are often involved in criminal activities? Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com A Black hats B White hats C Suicide hackers D Script kiddies - Answer -A John, a professional hacker, has launched an attack on a target organization to extract sensitive information. He was successful in launching the attack and gathering the required information. He is now attempting to hide the malicious acts by overwriting the server, system, and application logs to avoid suspicion. Which of the following phases of hacking is John currently in? A Maintaining access B Scanning C Clearing tracks D Gaining access - Answer -C Which of the following risk management phases involves selecting and implementing appropriate controls for the identified risks to modify them? A Risk tracking and review B Risk identification C Risk treatment D Risk assessment - Answer -C In which of the following incident handling and response phases are the identified security incidents analyzed, validated, categorized, and prioritized? A Incident recording and assignment B Incident triage C Containment D Eradication Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com
CourseHero & Studypool Unlocks
Get Unlocked CourseHero and Studypool documents files instantly to your email, simply by pasting your link and clicking "Unlock Now". Learn more on how to unlock here.