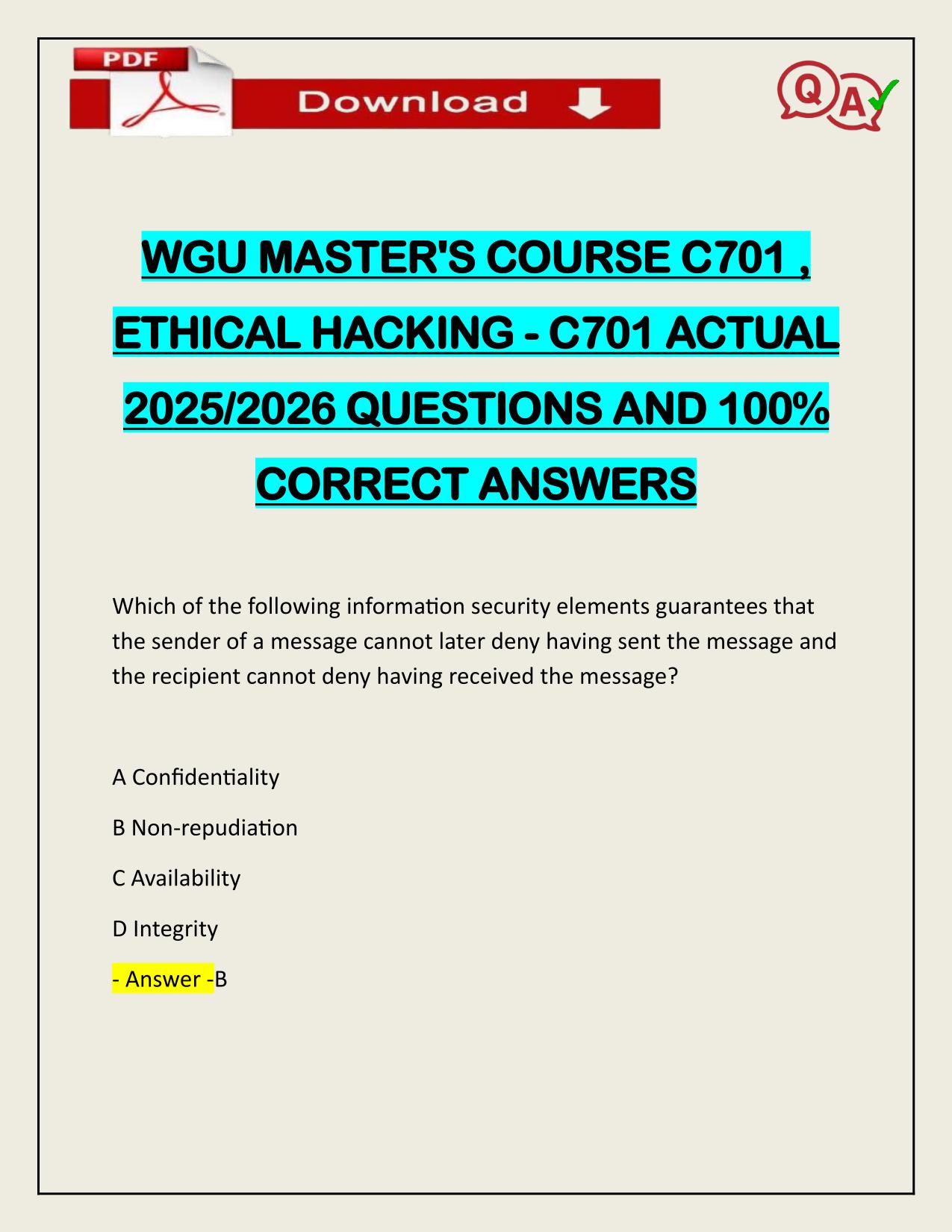
2025/2026 WGU MASTER'S COURSE C701 - ETHICAL HACKING
Course:
WGU MASTERS COURSE
Institution:
WGU MASTERS COURSE
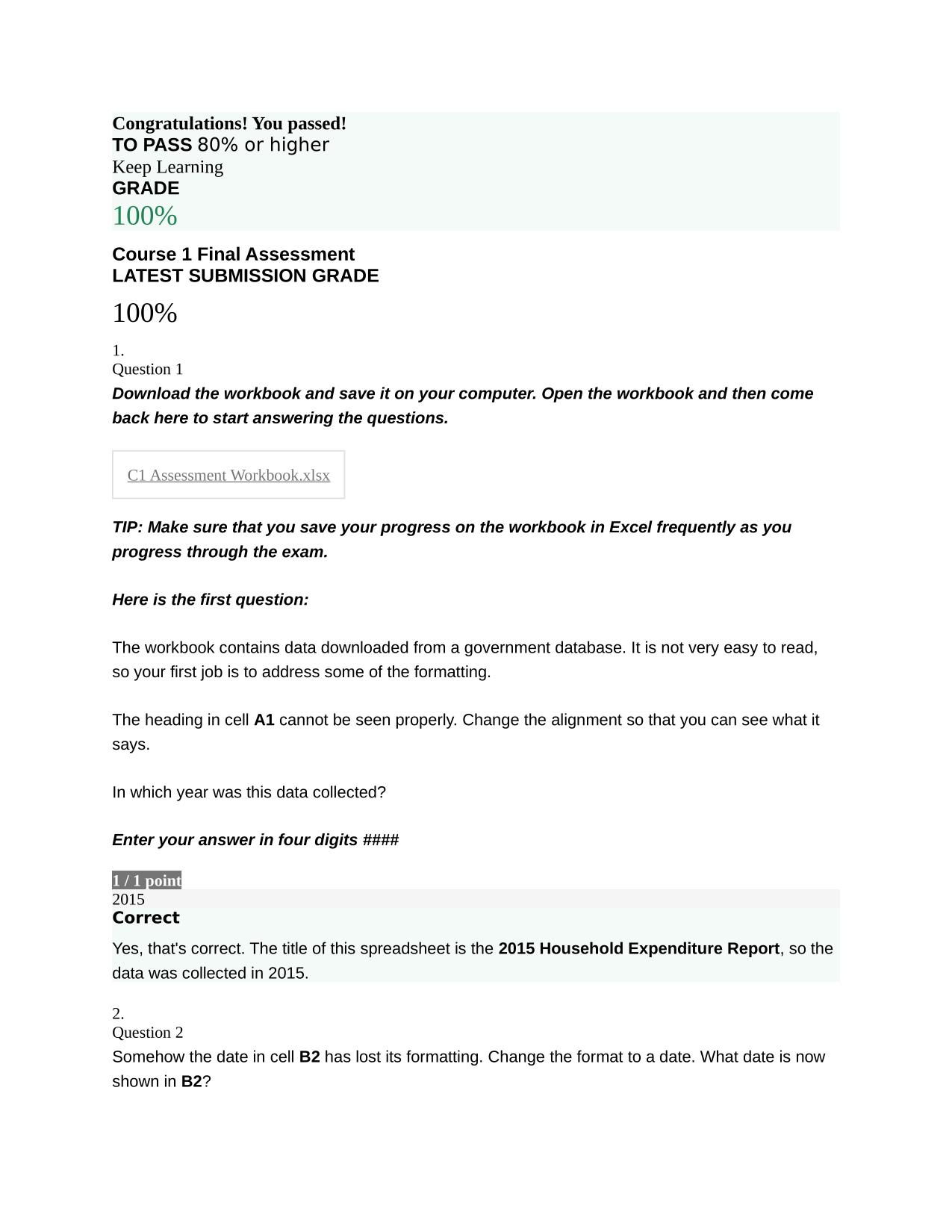
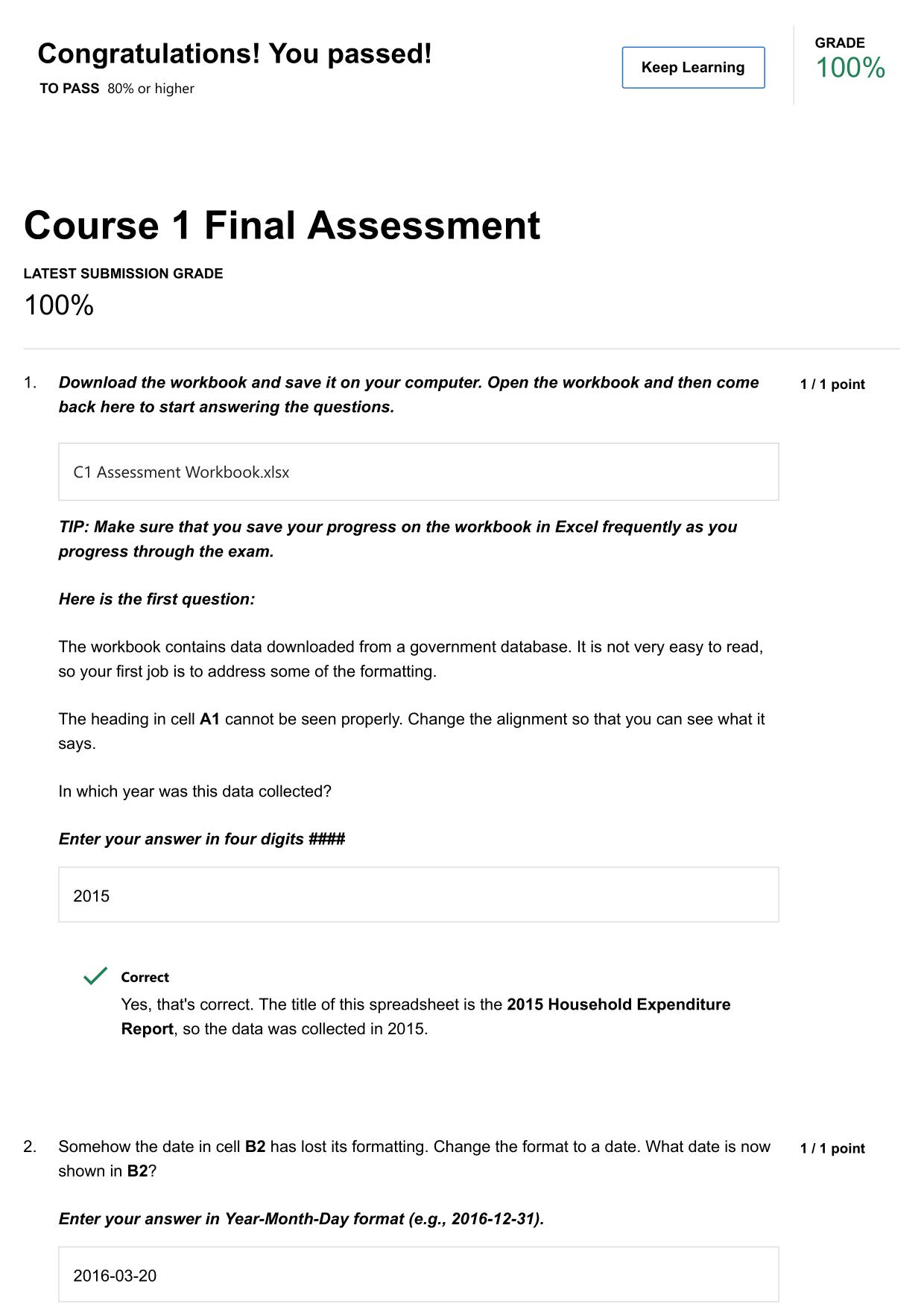
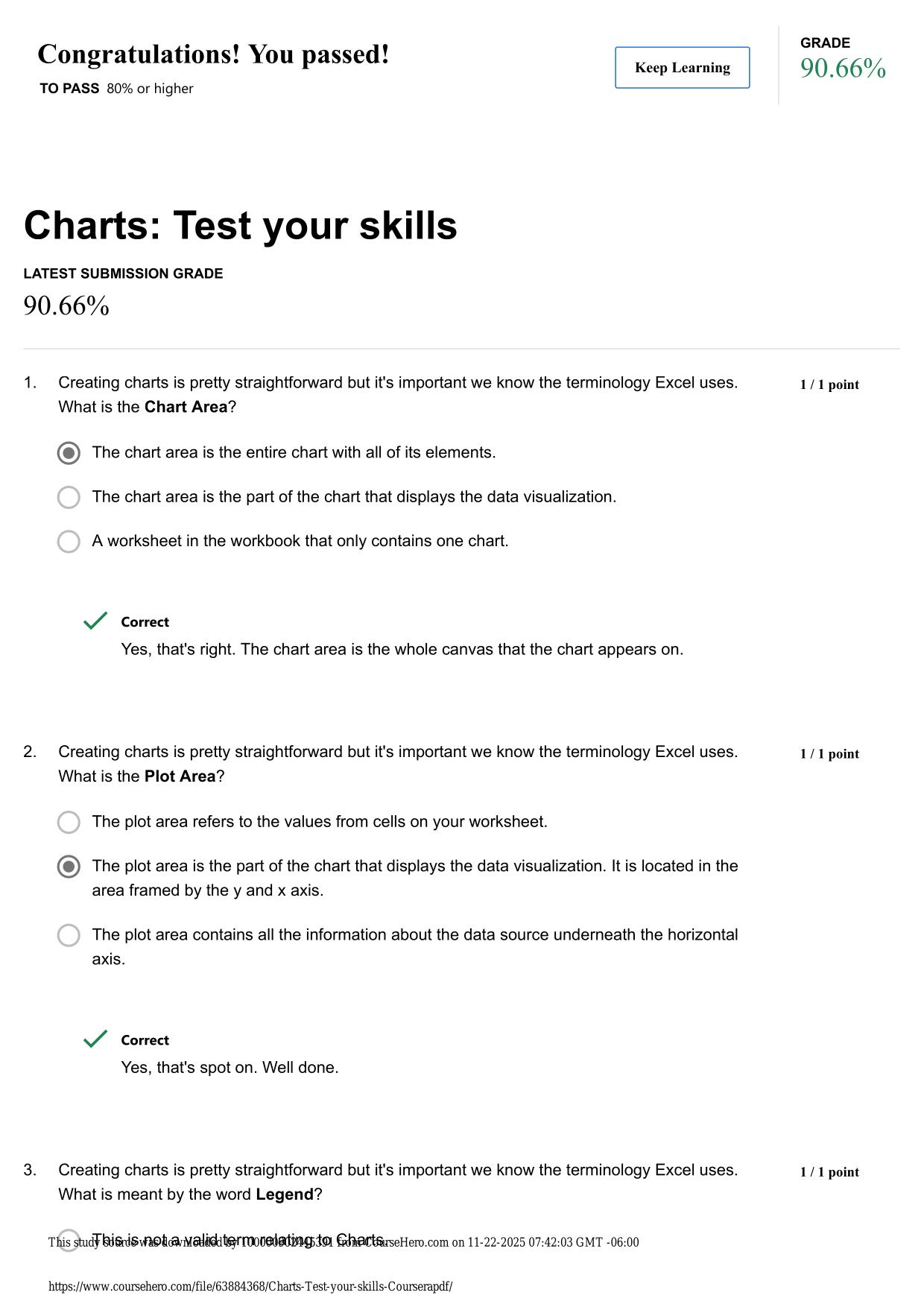
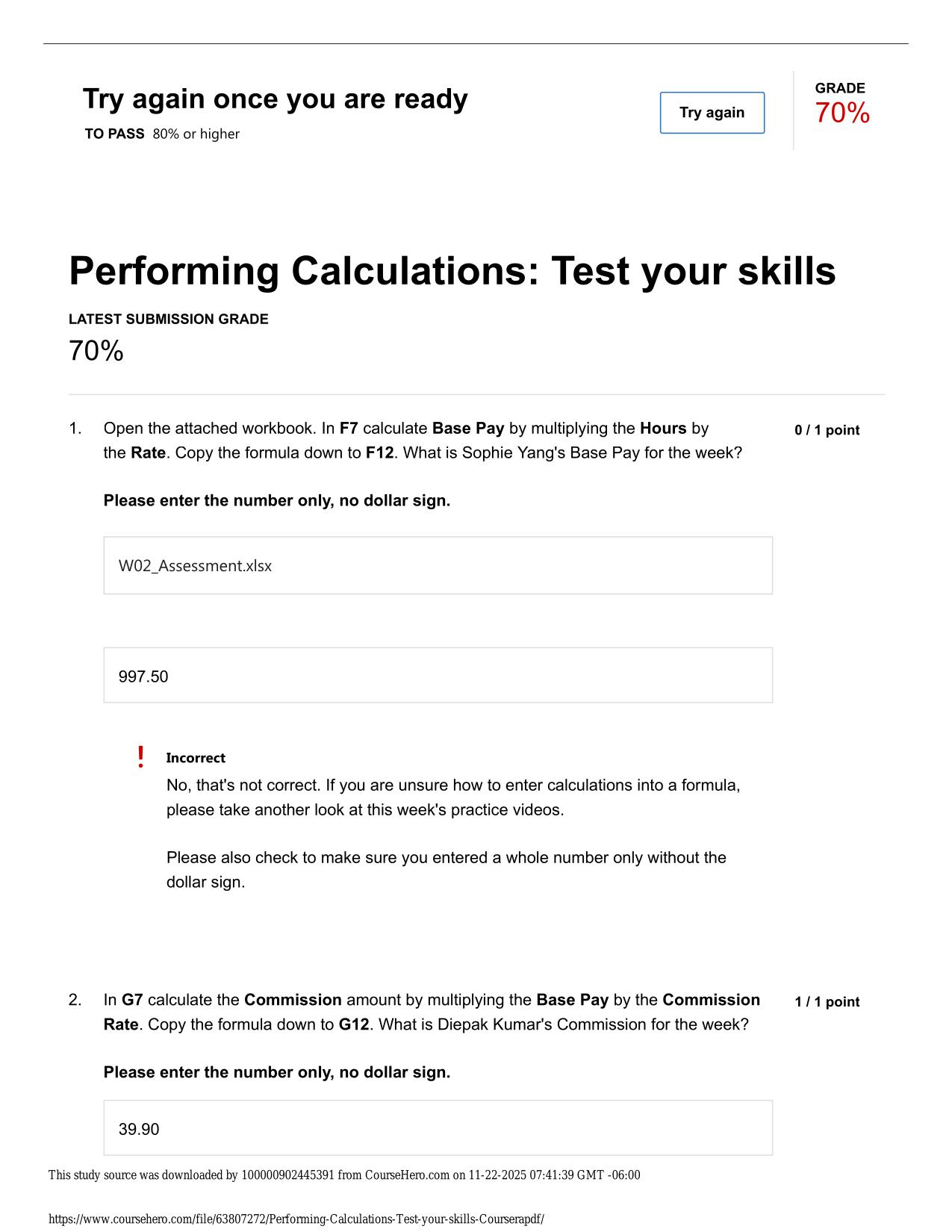
2025/2026 WGU MASTER'S COURSE C701 - ETHICAL HACKING ACTUAL QUESTIONS AND 100% CORRECT ANSWERS Because attackers break into systems for various reasons, it is important for information security professionals to understand how malicious hackers exploi...
After purchase, you get:
✅ Instant PDF Download
✅ Verified answer explanations
✅ Refund if not Satisfied
✅ Prepared for 2025/2026 test cycle
Overview
Learners gain valuable practice with question types commonly used on official / WGU excel at'S COURSE C701 - ETHICAL HACKING exams. From multiple-choice to case studies, you'll encounter the full range of formats used in actual assessments. This all-inclusive exposure prevents surprises on test day and builds adaptability in your approach. Students often mention how this variety keeps their study sessions interesting and engaging over weeks of preparation.
Who Is This For?
directed toward aspirants who want curated, mistake-free, and carefully formatted revision material for / WGU learn thoroughly'S COURSE C701 - ETHICAL HACKING. Users appreciate the attention to detail and accuracy. The clean presentation makes studying more streamlined and less frustrating.
Related Keywords
Detailed Study Description
Frequently Asked Questions
Document Information
| Uploaded on: | October 27, 2025 |
| Last updated: | November 17, 2025 |
| Number of pages: | 252 |
| Written in: | 2025/2026 |
| Type: | Exam (elaborations) |
| Contains: | Questions & Answers |
| Tags: | 2025/2026 WGU MASTER'S COURSE C701 - ETHICAL HACKING ACTUAL QUESTIONS AND 100% CORRECT ANSWERS Because attackers break into systems for various reasons, it is important for information security professionals to understand how malicious hackers exploit systems and the probable reasons behind the attacks. A True B False - Answer -A Information security refers to ________ or ________ information and information systems that use, store, and transmit information from unauthorized access, disclosure, alteration, and destructio |
Seller Information

AdelineJean
User Reviews (0)
Exam (Elaborations)
$11.00
Bundle Deal! Get all 7 docs for just $24.00
Add to Cart
100% satisfaction guarantee
Refund Upon dissatisfaction
Immediately available after purchase
Available in Both online and PDF
$11.00
| 0 sold
Discover More resources
Available in a Bundle
Inside The Document
2025/2026 WGU MASTER'S COURSE C701 - ETHICAL HACKING ACTUAL QUESTIONS AND 100% CORRECT ANSWERS Because attackers break into systems for various reasons, it is important for information security professionals to understand how malicious hackers exploit systems and the probable reasons behind the attacks. A True B False - Answer -A Information security refers to ________ or ________ information and information systems that use, store, and transmit information from unauthorized access, disclosure, alteration, and destruction. A compiling / securing B imaging / shielding C duplicating / saving D protecting / safeguarding - Answer -D Information is not the critical asset that organizations need to secure. A False B True - Answer -A ________ is the part of a malware or an exploit that performs the intended malicious actions, which can include creating backdoor access to a victim's machine, damaging or deleting files, and data theft. A Payload B Vulnerability Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com C Exploit D Hack value - Answer -A In a ________, the attacker exploits vulnerabilities in a computer application before the software developer can release a patch for them. A payload B zero-day attack C hack value D vulnerability - Answer -B Information security is defined as "a state of well-being of information and infrastructure in which the possibility of theft, tampering, and disruption of information and services is kept low and tolerable." A False B True - Answer -B Information security relies on four major elements: confidentiality, integrity, availability, and authenticity. A True B False - Answer -B ________ is the assurance that the information is accessible only to those authorized to have access. A Availability B Confidentiality C Authenticity D Integrity - Answer -B Confidentiality controls include data classification, data encryption, and proper equipment disposal. Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com
CourseHero & Studypool Unlocks
Get Unlocked CourseHero and Studypool documents files instantly to your email, simply by pasting your link and clicking "Unlock Now". Learn more on how to unlock here.