CS 6262 NETWORK SECURITY QUIZZES ACTUAL 2025/2026 Q&A
Course:
NETWORK SECURITY
Institution:
NETWORK SECURITY
CS 6262 NETWORK SECURITY QUIZZES ACTUAL 2025/2026 QUESTIONS AND 100% CORRECT ANSWERS T/F: Unlike UDP, TCP has the necessary safeguards in place to prevent network DoS. - Answer -False Which of the following actors are part of the cyber crime undergro...
After purchase, you get:
✅ Instant PDF Download
✅ Verified answer explanations
✅ Refund if not Satisfied
✅ Prepared for 2025/2026 test cycle
Overview
This material encourages active engagement through solution walkthroughs that reinforce both theory and application. Rather than passively reading, you're constantly interacting with the content through problem-solving. This active learning approach makes study sessions more dynamic and information more memorable. Many learners find they retain knowledge better when they've worked through problems rather than just reviewed notes.
Who Is This For?
A practical option for those preparing for school assessments, standardized tests, or professional exams in NETWORK SECURITY. The material has proven effective across different educational contexts. Users appreciate its straightforward, no-nonsense approach to test preparation.
Related Keywords
Detailed Study Description
Frequently Asked Questions
Document Information
| Uploaded on: | October 31, 2025 |
| Last updated: | November 17, 2025 |
| Number of pages: | 22 |
| Written in: | 2025/2026 |
| Type: | Exam (elaborations) |
| Contains: | Questions & Answers |
| Tags: | CS 6262 NETWORK SECURITY QUIZZES ACTUAL 2025/2026 QUESTIONS AND 100% CORRECT ANSWERS T/F: Unlike UDP, TCP has the necessary safeguards in place to prevent network DoS. - Answer -False Which of the following actors are part of the cyber crime underground economy? - Answer -Exploit Developers, Botnet |
Seller Information

AdelineJean
User Reviews (0)
Exam (Elaborations)
$9.00
Bundle Deal! Get all 5 docs for just $17.50
Add to Cart
100% satisfaction guarantee
Refund Upon dissatisfaction
Immediately available after purchase
Available in Both online and PDF
$9.00
| 0 sold
Discover More resources
Available in a Bundle
Inside The Document
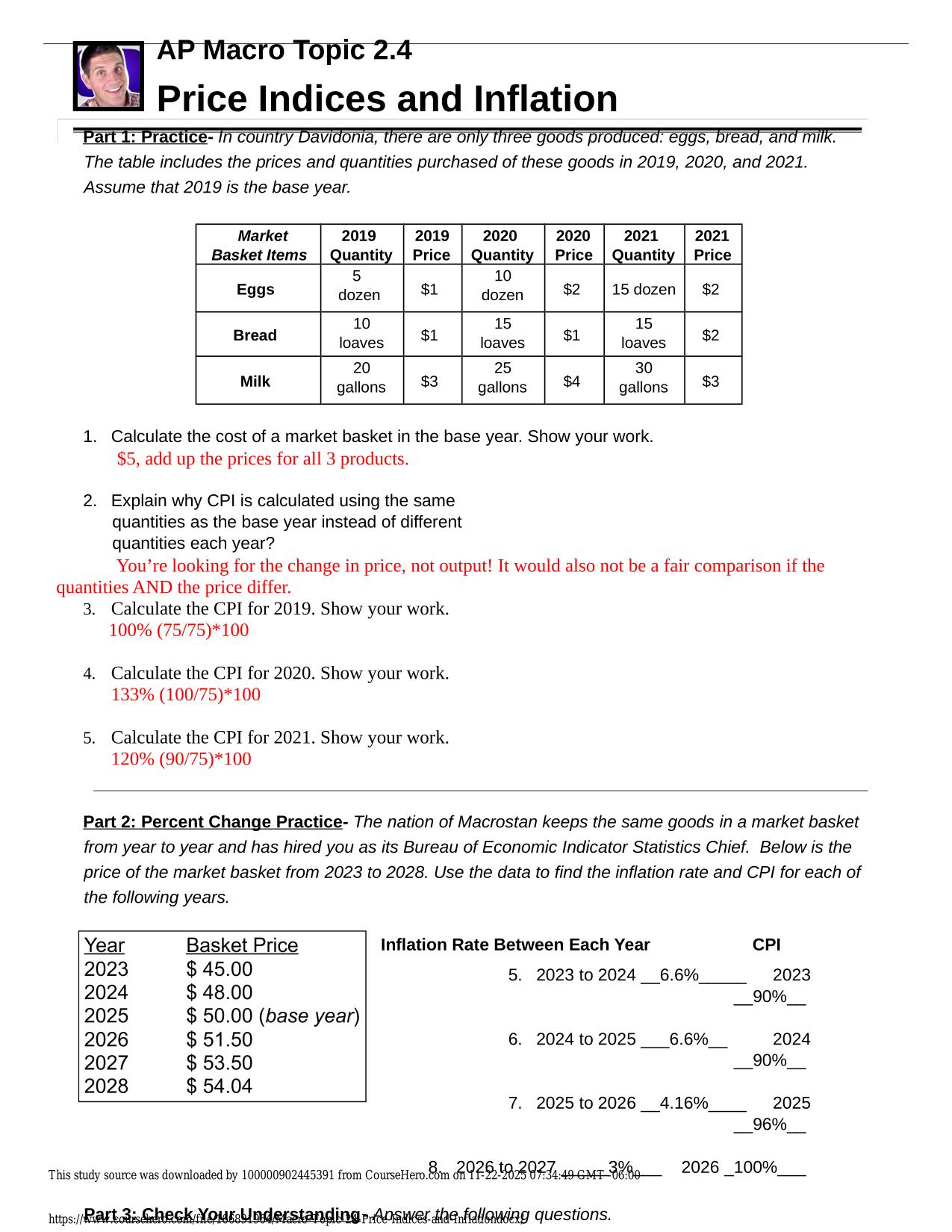
CS 6262 NETWORK SECURITY QUIZZES ACTUAL 2025/2026 QUESTIONS AND 100% CORRECT ANSWERS T/F: Unlike UDP, TCP has the necessary safeguards in place to prevent network DoS. - Answer -False Which of the following actors are part of the cyber crime underground economy? - Answer -Exploit Developers, Botnet Masters, Spammers Which of the following is/are NOT a potential network level DoS mitigation? (hints: Which method is not for mitigating Dos? Which method is used for mitigating DoS attacks at the application level instead?) - Client Puzzles - CAPTCHAs - Use only TCP - Increase UDP 3-way handshake - Source Identification - Answer -CAPTCHAs, Use only TCP, Increase UDP 3-way handshake T/F: In 2015, GitHub was a victim of a distributed denial of service attack. The attackers injected malicious JavaScript code in GitHub's web pages. - Answer -False T/F: Unlike UDP, TCP has the necessary safeguards in place to prevent network DoS - Answer -False Select tools used for scanning in the Penetration methodology - nmap Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com - john the ripper - siphon - fping - Answer -- nmap - siphon - fping Suppose that a company owns two websites: A.com and B.com. Where a website of A.com dynamically gets resources from B.com via AJAX requests depending on the user's input, which of the following mechanisms can be adopted by the developers of B.com to allow A.com to gain access to their resources? - Cross Origin Resource Sharing - Content Security Policy - Allow Page Access Policy - Same Origin Policy - Answer -Cross Origin Resource Sharing Which of the following is/are social engineering techniques: - Impersonation of Help Desk - Email Attachments - Tailgating - Pop-up windows - Answer -Impersonation of Help Desk, Email Attachments, Tailgating, Pop-up windows T/F: Subresource integrity uses a cryptographic hash to ensure that webpage subresources have not changed on the way. - Answer -True Which of the following is true for modern browsers that meet RFC6265, assuming the following cookie information? Cookie 1 information: name=cookie1; domain: cs6262.gatech.com; path: /canvas Cookie 2 information: name=cookie2; domain: cs6262.gatech.edu; path: / - The browser can send cookie2 to mail.cs6262.gatech.edu host Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com
CourseHero & Studypool Unlocks
Get Unlocked CourseHero and Studypool documents files instantly to your email, simply by pasting your link and clicking "Unlock Now". Learn more on how to unlock here.