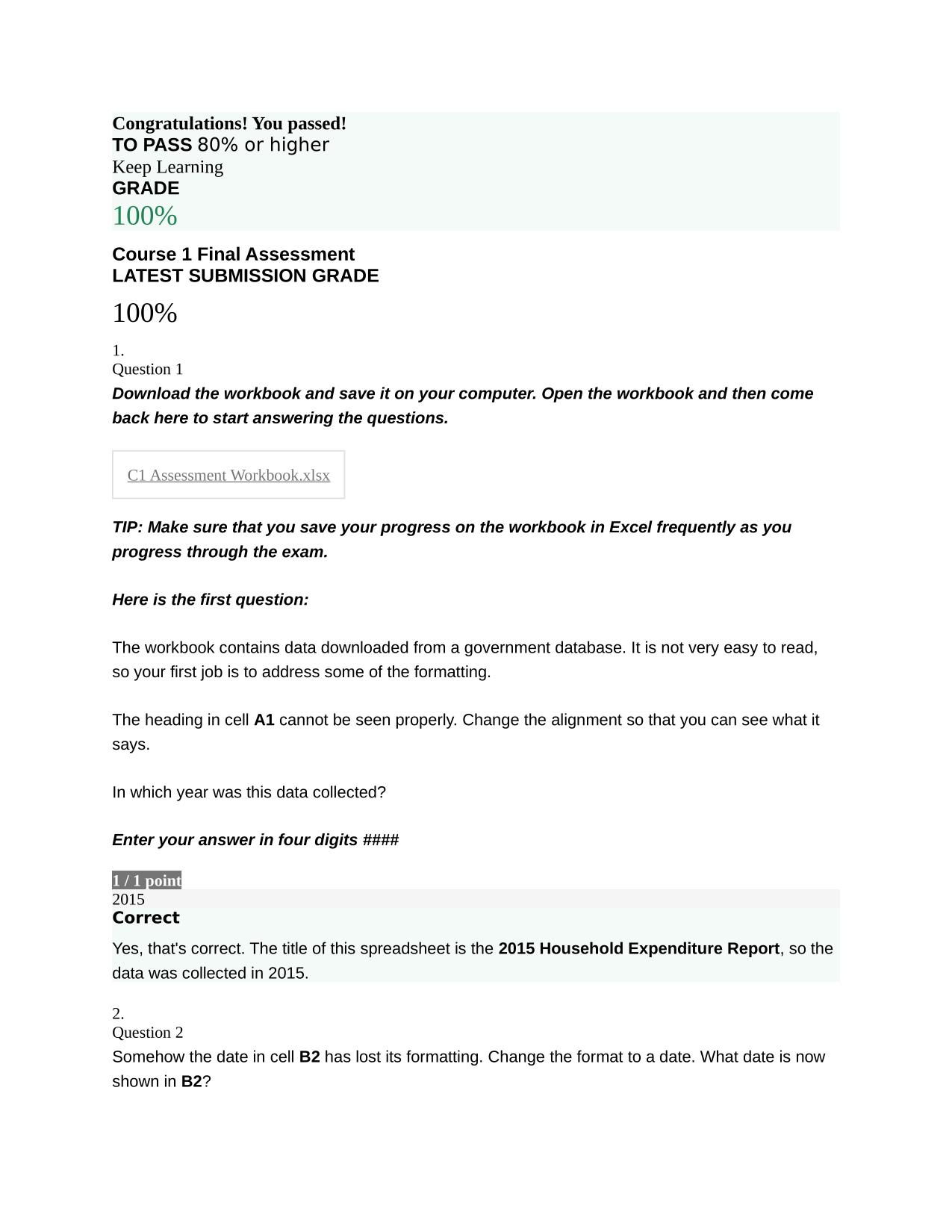
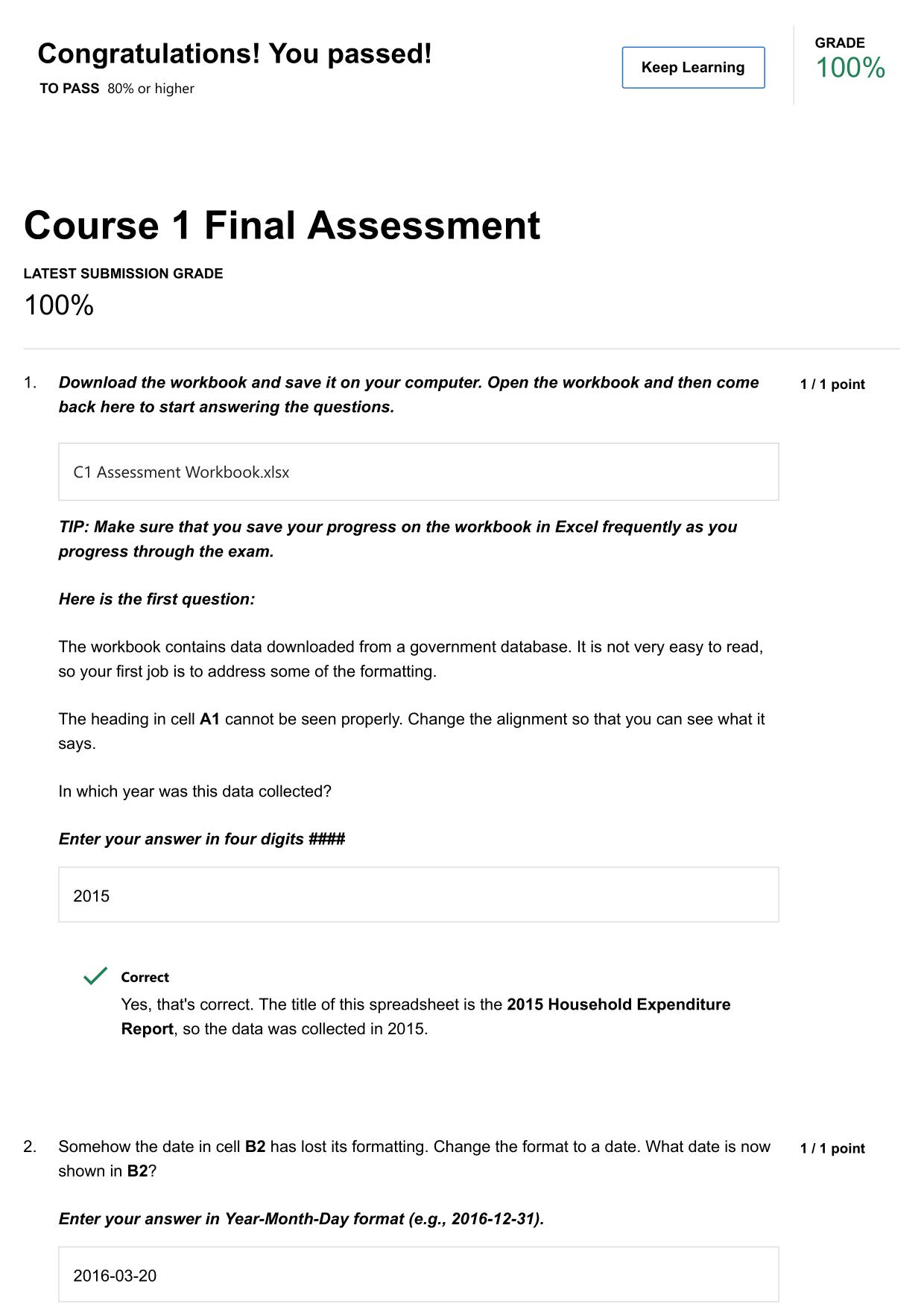
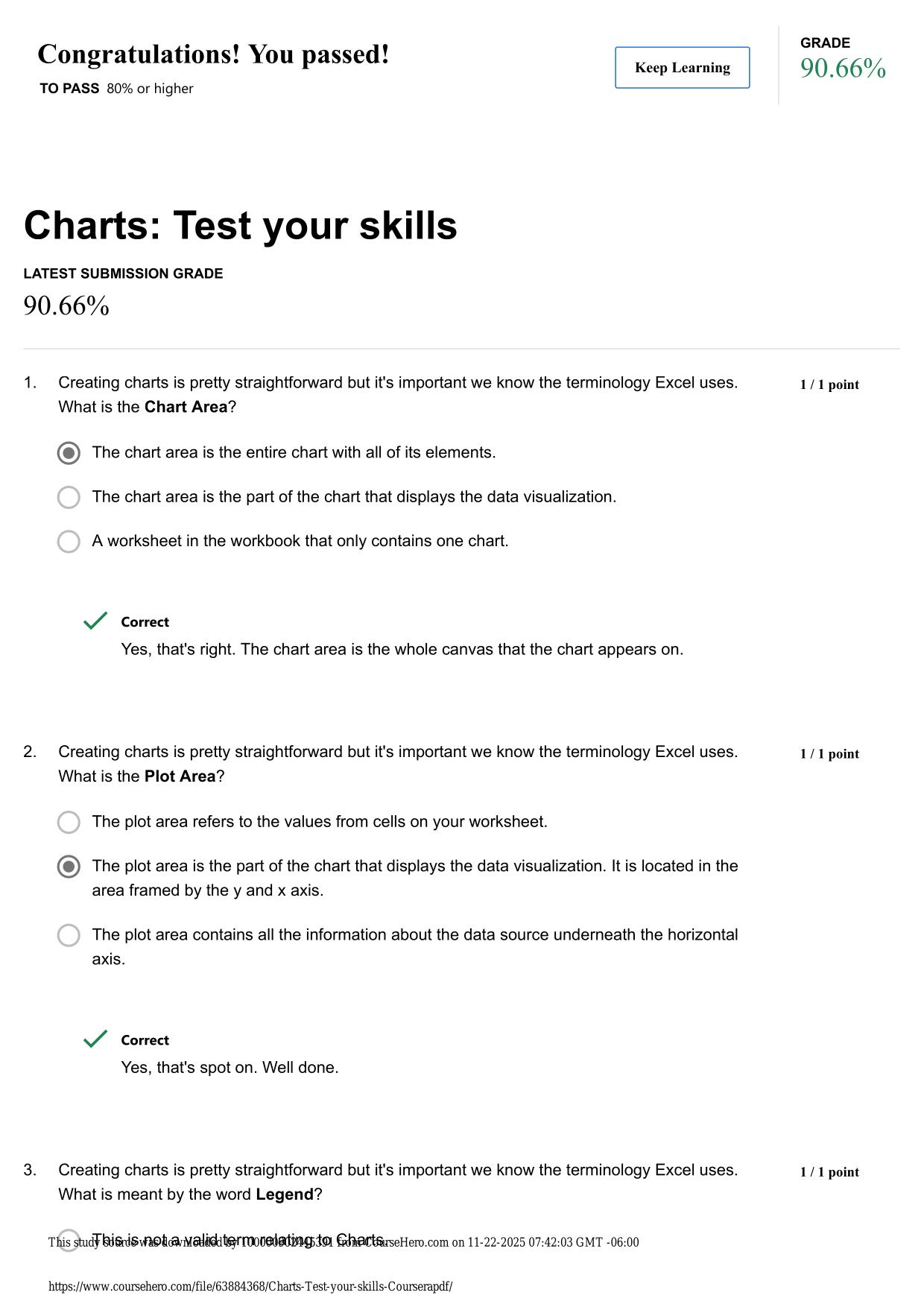
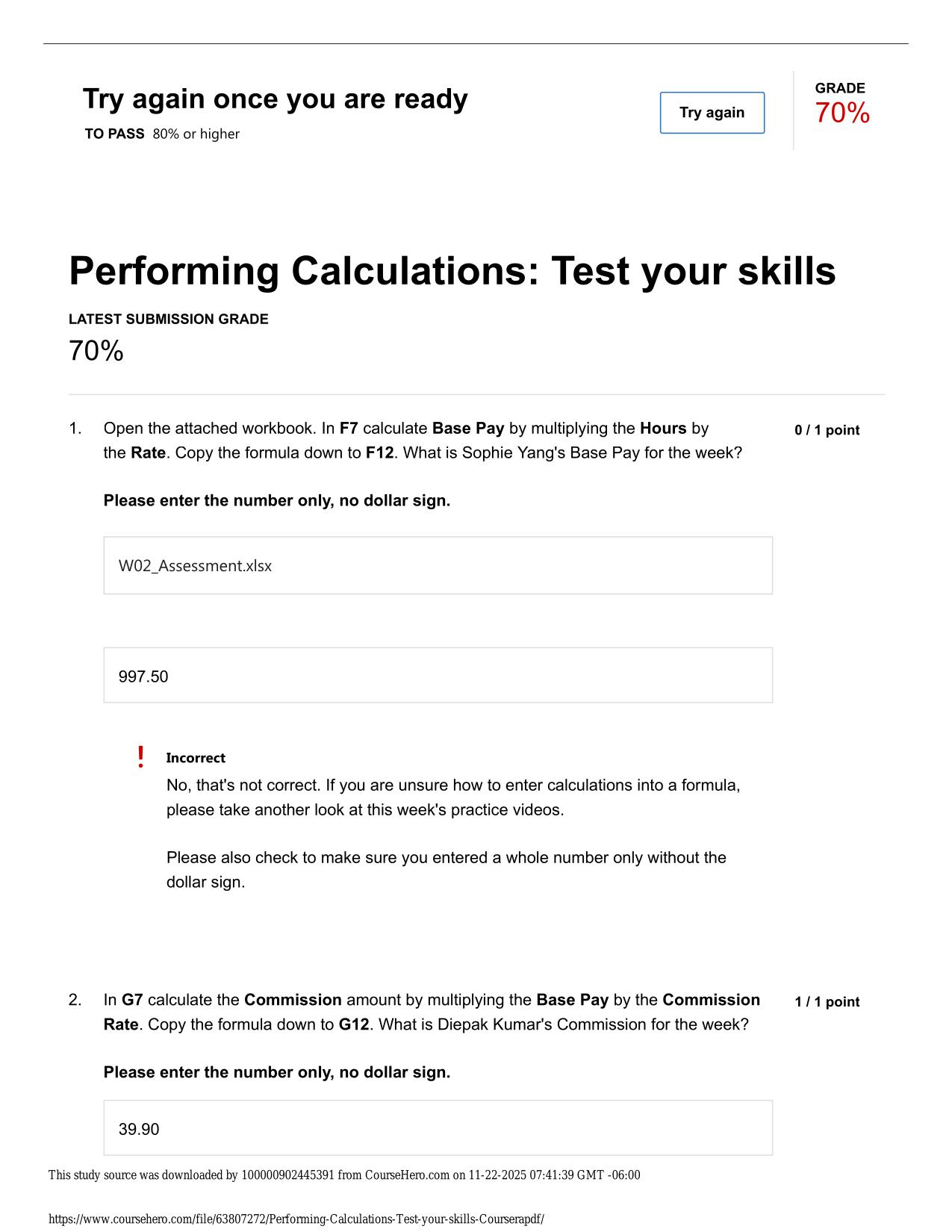
CS 423 NETWORK SECURITY: MIDTERM ACTUAL 2025/2026 UPDATE
Course:
NETWORK SECURITY
Institution:
NETWORK SECURITY
CS 423 NETWORK SECURITY: MIDTERM ACTUAL 2025/2026 QUESTIONS AND 100% CORRECT ANSWERS What is the level of security provided by double DES? - Answer -2^56 (due to meet-in-the-middle attack) What is a digital certificate and what is it used for? - Answ...
After purchase, you get:
✅ Instant PDF Download
✅ Verified answer explanations
✅ Refund if not Satisfied
✅ Prepared for 2025/2026 test cycle
Overview
Explanations help bridge the gap between theoretical learning and practical application—critical for exam success. You're learning how to take classroom knowledge and apply it to real testing situations. This translation skill is exactly what many students struggle with when facing complete exams. The practical focus ensures you can actually use what you've learned when it matters most.
Who Is This For?
Well-suited to learners who struggle with test anxiety and benefit from predictable, exam-style practice formats. Numerous students have reported feeling calmer during actual exams after using these materials. The familiar format reduces surprises on test day. Suitable for college students, learners, and healthcare practitioners needing clear, exam-focused study material in NETWORK SECURITY. People appreciate how it cuts through unnecessary information. The focused content addresses exactly what test-takers need to know.
Related Keywords
Detailed Study Description
Frequently Asked Questions
Document Information
| Uploaded on: | October 31, 2025 |
| Last updated: | November 17, 2025 |
| Number of pages: | 19 |
| Written in: | 2025/2026 |
| Type: | Exam (elaborations) |
| Contains: | Questions & Answers |
| Tags: | CS 423 NETWORK SECURITY: MIDTERM ACTUAL 2025/2026 QUESTIONS AND 100% CORRECT ANSWERS What is the level of security provided by double DES? - Answer -2^56 (due to meet-in-the-middle attack) What is a digital certificate and what is it used for? - Answer -It is a digital document, signed by a trusted third party (certificate authority) establishing t |
Seller Information

AdelineJean
User Reviews (0)
Exam (Elaborations)
$9.00
Bundle Deal! Get all 5 docs for just $17.50
Add to Cart
100% satisfaction guarantee
Refund Upon dissatisfaction
Immediately available after purchase
Available in Both online and PDF
$9.00
| 0 sold
Discover More resources
Available in a Bundle
Inside The Document
CS 423 NETWORK SECURITY: MIDTERM ACTUAL 2025/2026 QUESTIONS AND 100% CORRECT ANSWERS What is the level of security provided by double DES? - Answer -2^56 (due to meet-in-the-middle attack) What is a digital certificate and what is it used for? - Answer -It is a digital document, signed by a trusted third party (certificate authority) establishing the binding between a subject's identity and the subject's public key. It is used to establish the authenticity of users' public keys A pixel map (consisting of a matrix corresponding to the pixel values) of image in Figure (a) was encrypted with Triple-DES in two different modes, ECB and CBC, to obtain the images in Figures (b) and (c) "not" necessarily in that order. Which mode does Figure (b) correspond to? Figure (c)? Explain why. - Answer -Figure B: CBC; Figure C: ECB; ECB encrypt the same planter blocks to same ciperhtext blocks every time. Hence, it preserves the patterns of plaintext into cipher text (e.g., the same pixel values in the plaintext image get mapped to the same pixel values in the cipher text image). In contrast, CBC is randomized tend due to the use of an IV (and chaining), the same plaintext gets encrypted to entirely different cipher text each time. A pixel map (consisting of a matrix corresponding to the pixel values) of image in Figure (a) was encrypted with Triple-DES in two different modes, ECB and CBC, to obtain the images in Figures (b) and (c) "not" necessarily in that order. Which image, B or C, represents a "good" encryption? Explain why. - Answer -Image B represents a good encryption because there ar no decipherable patterns in the encrypted image. In case of image C, the pattern of pixels in original image is carried over to the encrypted image due to lack of randomization. Hence, an adversary can deduce the Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com original pixel pattern if he observes the same pattern in the encrypted image. Thus, image B is secure (against CPA) whereas image C is not. Does a MAC scheme provide non-reputation? Explain your answer. - Answer -No, Since the MAC is generated using a symmetric key (shared between the sender and the verifier), either can create it and keep on blaming that the other created it True or False: PGP uses RSA to encrypt the email messages. - Answer -False, RSA is used to agree upon a symmetric key and symmetric key algorithm is used to encrypt the message. True or False: PGP uses RSA to sign the email messages. - Answer -True In which order, does PGP perform message encryption, signature, and compression operations? - Answer -Signature, compression, encryption Alice's RSA public key is N=15 and e = 3. Show how an attacker (who knows N and e), can learn Alice's private key d. Show all steps. It is not necessary to calculate the value of d, just show the steps needed. - Answer -N = 15, e = 3 So public key would be the pair (e, N) i.e. (3, 15) The private key 'd' is the inverse of 'e' in Z_phi(n) so we first need to calculate phi(n). The attacker knows that N is a product of two primes so if he is able to factorize N as p*q where p and q are primes, he can get phi(n). Factoring N=15, we get p=3, q = 5 (both are prime). So phi(n) = (p-1)(q-1) = (3-1)(5-1) = 2 * 4 = 8. Now the attacker just needs to find the inverse of 'e' in Z_phi(n) i.e. Z_8 = {0,1,2,3,4,5,6,7}. For 'd' to be inverse of e in Z_8, ed = 1(mod 8) or 3d = 1 (mod 8). d = 3 satisfies the above equation because 3*3 = 9 = 1(mod 8). So Alice's private key is 3. Describe how a DNS Reflection Attack works (a form of DoS attack). - Answer -The attacker sends a large number of queries to DNS servers spoofing the IP address of victim machine. All the DNS server responses will then be sent/reflected back to the victim's machine, probably Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com
CourseHero & Studypool Unlocks
Get Unlocked CourseHero and Studypool documents files instantly to your email, simply by pasting your link and clicking "Unlock Now". Learn more on how to unlock here.