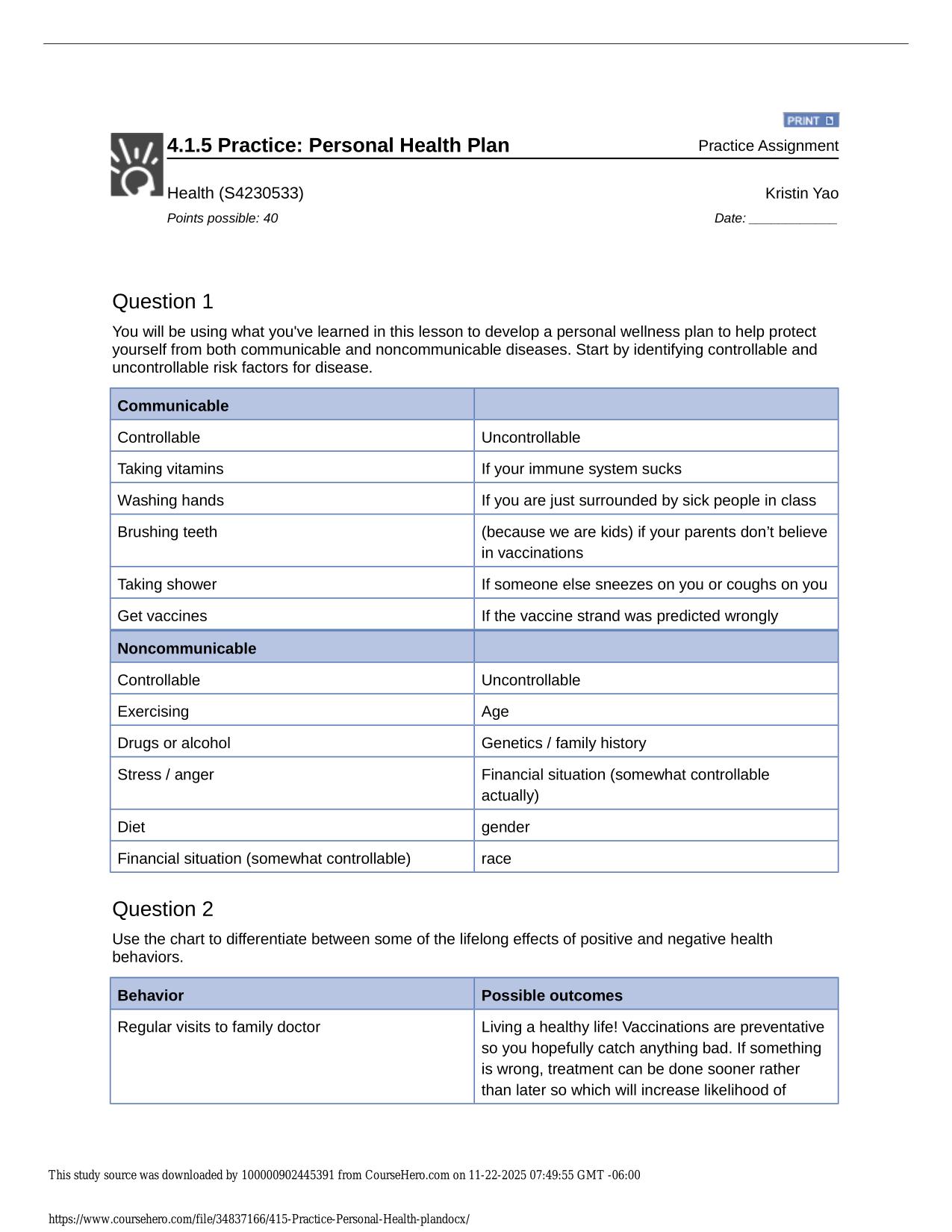
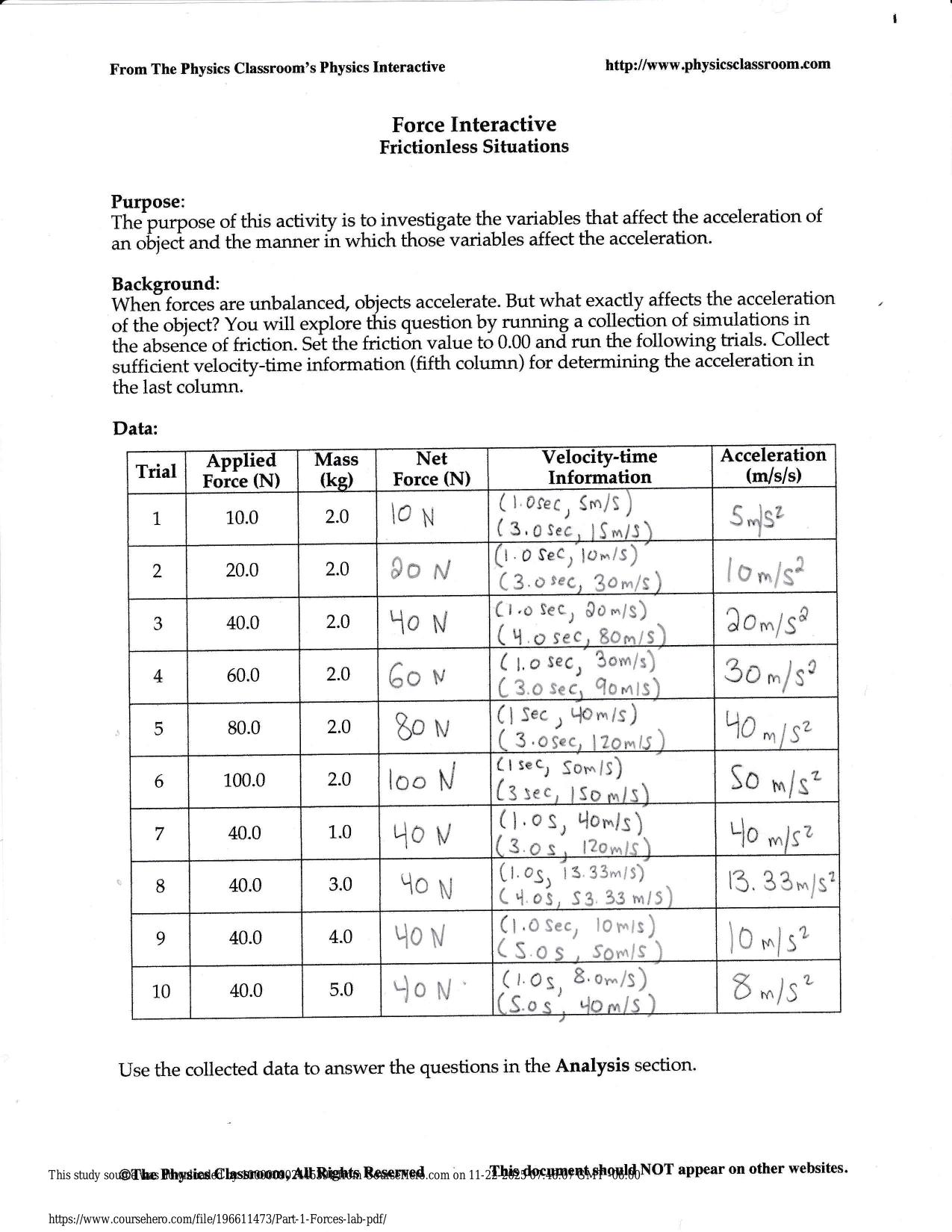
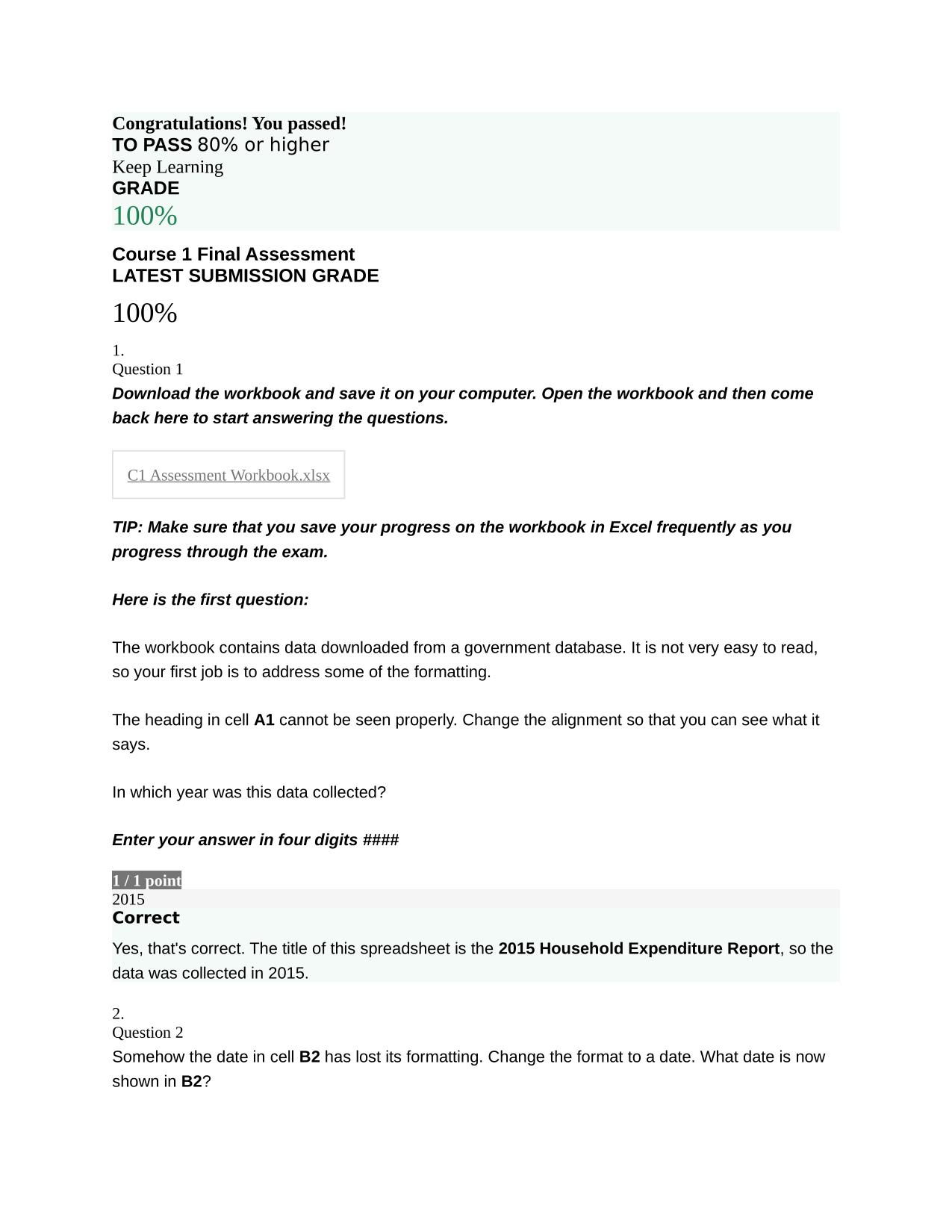
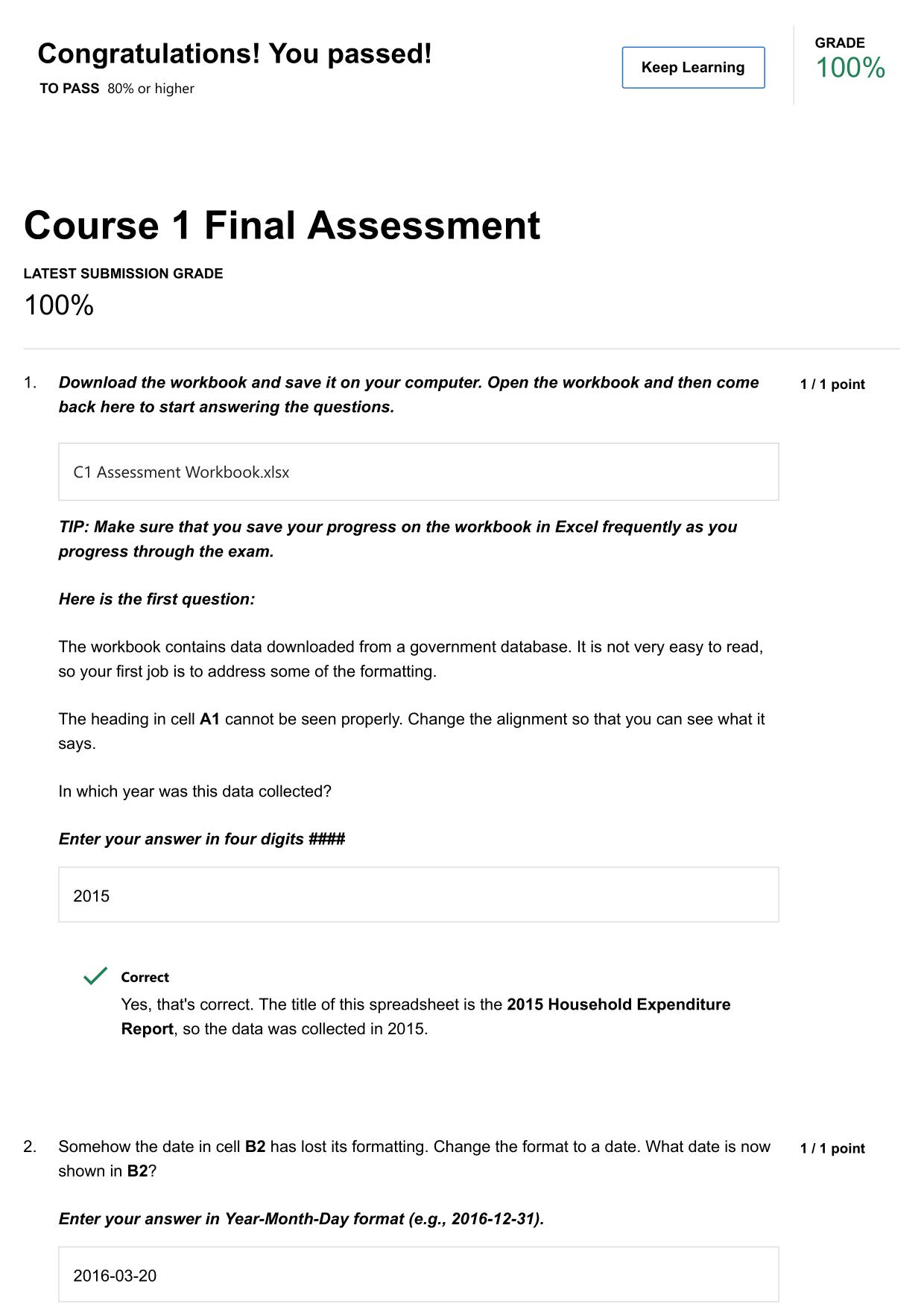
QUIZ COMPTIA SECURITY+ SYO- 601 POST-ASSESSMENT QUIZ ACTUAL 2025/2026
Course:
SY0-601 COMPTIA SECURITY
Institution:
SY0-601 COMPTIA SECURITY
QUIZ: COMPTIA SECURITY+ SYO- 601 POST-ASSESSMENT QUIZ ACTUAL 2025/2026 QUESTIONS AND 100% CORRECT ANSWERS Typically, certain employees of an organization get texts that update them on various IT activities. If there is a support ticket or downtime, t...
After purchase, you get:
✅ Instant PDF Download
✅ Verified answer explanations
✅ Refund if not Satisfied
✅ Prepared for 2025/2026 test cycle
Overview
systematic practice sessions guide learners through progressive difficulty to build self-assurance gradually. Each level of challenge prepares you for the next, creating a natural learning progression. This incremental approach prevents frustration and keeps motivation high throughout your preparation. Many learners appreciate how this systematic practice makes their progress feel tangible and rewarding. QUIZ COMPTIA SECURITY+ SYO- 601 POST-ASSESSMENT QUIZ ACTUAL 2025/2026 includes exam-relevant questions that help test-takers evaluate weaknesses and strengthen vital competencies. The clear answer explanations turn every mistake into a learning opportunity rather than a frustration. Many users keep notes on which areas need more attention, creating a personalized study plan based on actual performance. This responsive approach ensures you're always working on what matters most for your success.
Who Is This For?
Well-suited to learners who struggle with test anxiety and benefit from predictable, exam-style practice formats. Numerous students have reported feeling calmer during actual exams after using these materials. The familiar format reduces surprises on test day.
Related Keywords
Detailed Study Description
Frequently Asked Questions
Document Information
| Uploaded on: | October 26, 2025 |
| Last updated: | November 17, 2025 |
| Number of pages: | 24 |
| Written in: | 2025/2026 |
| Type: | Exam (elaborations) |
| Contains: | Questions & Answers |
| Tags: | QUIZ: COMPTIA SECURITY+ SYO- 601 POST-ASSESSMENT QUIZ ACTUAL 2025/2026 QUESTIONS AND 100% CORRECT ANSWERS Typically, certain employees of an organization get texts that update them on various IT activities. If there is a support ticket or downtime, they will receive texts to let them know about the activity. They have started to receive some messages via text instructing them to call the IT help desk at the provided number. When they call the help desk number, a recording asks them for their employee ID. |
Seller Information

AdelineJean
User Reviews (0)
Exam (Elaborations)
$9.00
Bundle Deal! Get all 3 docs for just $12.00
Add to Cart
100% satisfaction guarantee
Refund Upon dissatisfaction
Immediately available after purchase
Available in Both online and PDF
$9.00
| 0 sold
Discover More resources
Available in a Bundle
Inside The Document
QUIZ: COMPTIA SECURITY+ SYO601 POST-ASSESSMENT QUIZ ACTUAL 2025/2026 QUESTIONS AND 100% CORRECT ANSWERS Typically, certain employees of an organization get texts that update them on various IT activities. If there is a support ticket or downtime, they will receive texts to let them know about the activity. They have started to receive some messages via text instructing them to call the IT help desk at the provided number. When they call the help desk number, a recording asks them for their employee ID. Assuming that the IT department did not send those texts, which of the following social engineering attacks is this? - Answer -Smishing Which of the following social engineering attacks continues to be a primary weapon used by threat actors? - Answer -Phishing David, a software engineer, recently bought a brand new laptop because his enterprise follows the BYOD (bring your own device) model. David was part of a software development project where the software code was leaked before its release. Further investigation proved that a vulnerability in David's laptop caused the exposure. David insists he never used the laptop to access any network or integrate any devices, and the laptop was kept in a vault while not in use. Which of the following attack vectors was used by the threat actor? - Answer -c. Supply chain Which category of cybersecurity vulnerability is exploited by attackers before anyone else knows about it? - Answer -c. Zero day The company that developed the office productivity software used on both static and mobile devices by your organization has audited some code and noticed a potential security issue. To address the issue, they have released and automatically scheduled an update to ensure that all users receive it. Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com Which of the following might still be vulnerable after the patch? - Answer -c. Firmware Which of the following types of hackers are strongly motivated by ideology? - Answer -Hacktivists Which part of the NIST Cybersecurity frameworks defines the activities needed to attain the different cybersecurity results? - Answer -b. Framework core Which type of vulnerability scan mimics the work of a threat actor who has already exploited a vulnerability and compromised credentials to access the network? - Answer -b. Credentialed scan John is appointed as a vulnerability assessment engineer in a financial organization. An audit report published by a third-party auditing firm revealed that most of the web servers have cross-site scripting and XML entity injection vulnerabilities. John has been told to perform a vulnerability assessment on these servers to verify if the audit report is valid. He is also told that he should not attempt to engage or exploit any vulnerabilities. By applying his knowledge of vulnerability assessment concepts, which type of vulnerability scanning should John use? - Answer -d. Credentialed Quinton has been asked to analyze the TTPs of an attack that recently occurred and prepare an SOP to hunt for future treats. When researching the recent attack, Quinton discovered that after penetrating the system, the threat actor moved through the network using elevated credentials. Which technique was the threat actor using to move through the network? - Answer -b. Lateral movement Meta is a penetration testing engineer assigned to pen test the security firm's network. So far, she cannot tunnel through the network looking for additional systems accessible through advanced privileges. What should Meta do to gain repeated and long-term access to the system in the future? - Answer -b. Perform backdoor installation Shaun is an external penetration testing consultant. The Chief Information Security Officer (CISO) of the organization he is working Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com
CourseHero & Studypool Unlocks
Get Unlocked CourseHero and Studypool documents files instantly to your email, simply by pasting your link and clicking "Unlock Now". Learn more on how to unlock here.