FY24 CYBER AWARENESS CHALLENGE ACTUAL 2025/2026 CORRECTLY ANSWERED
Course:
CYBER AWARENESS CHALLENGE
Institution:
CYBER AWARENESS CHALLENGE
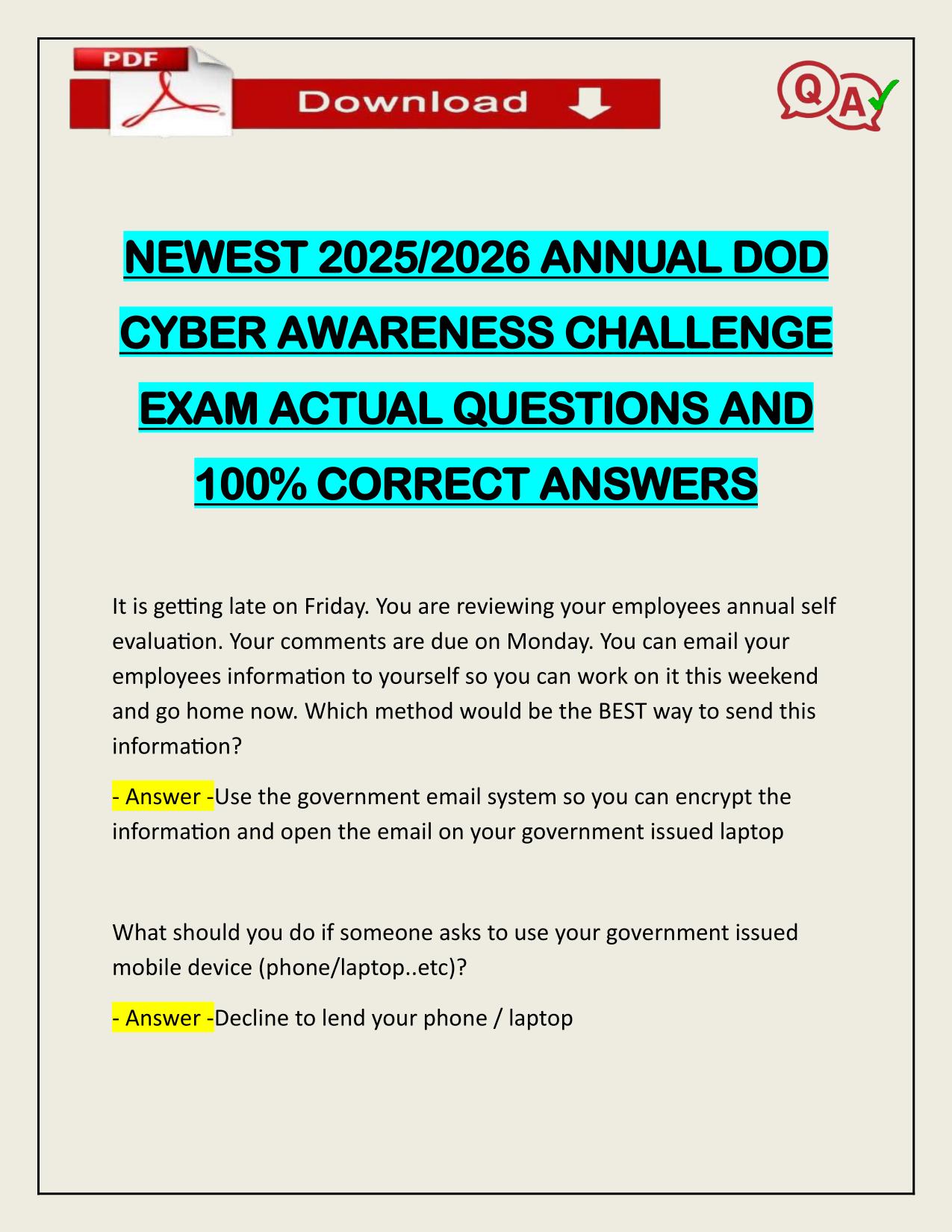
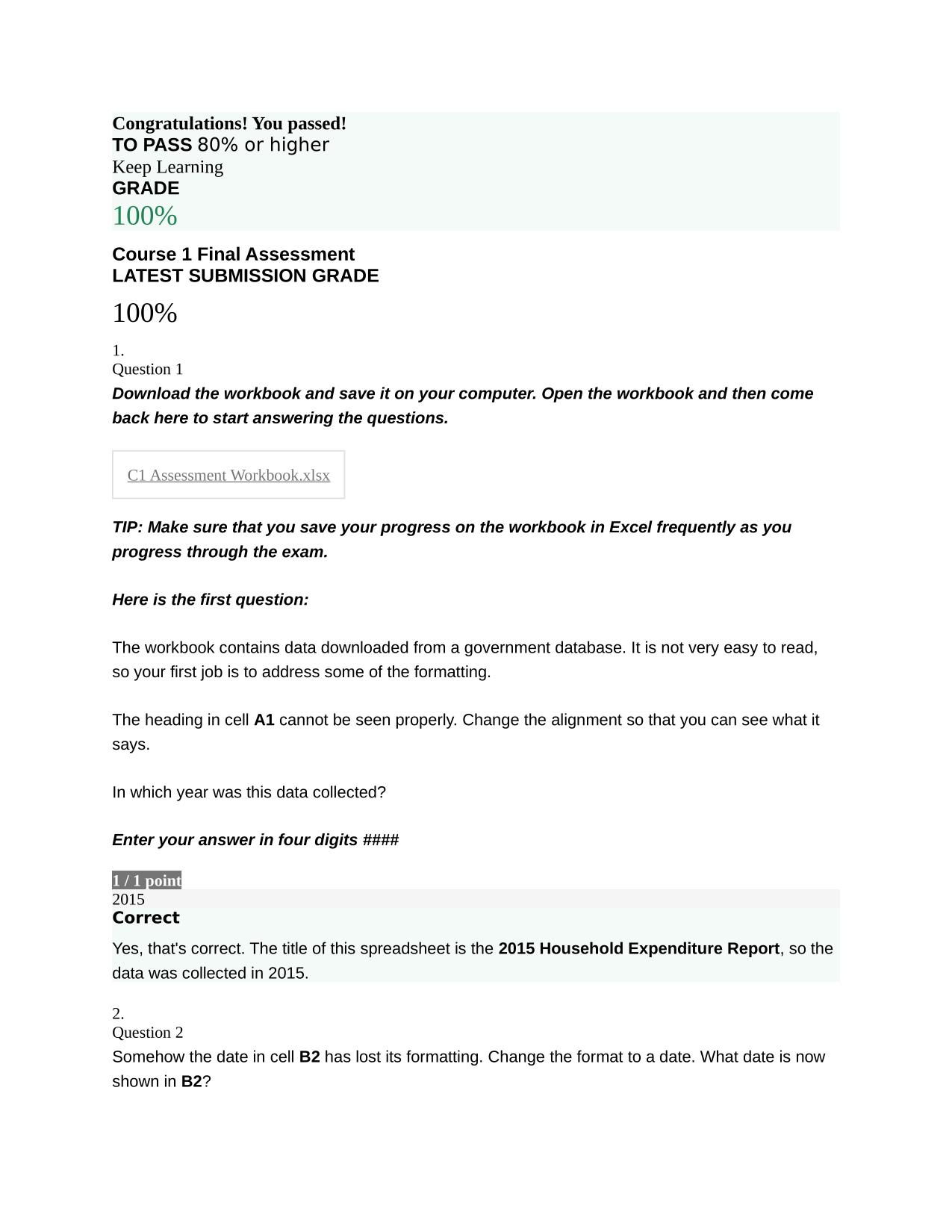
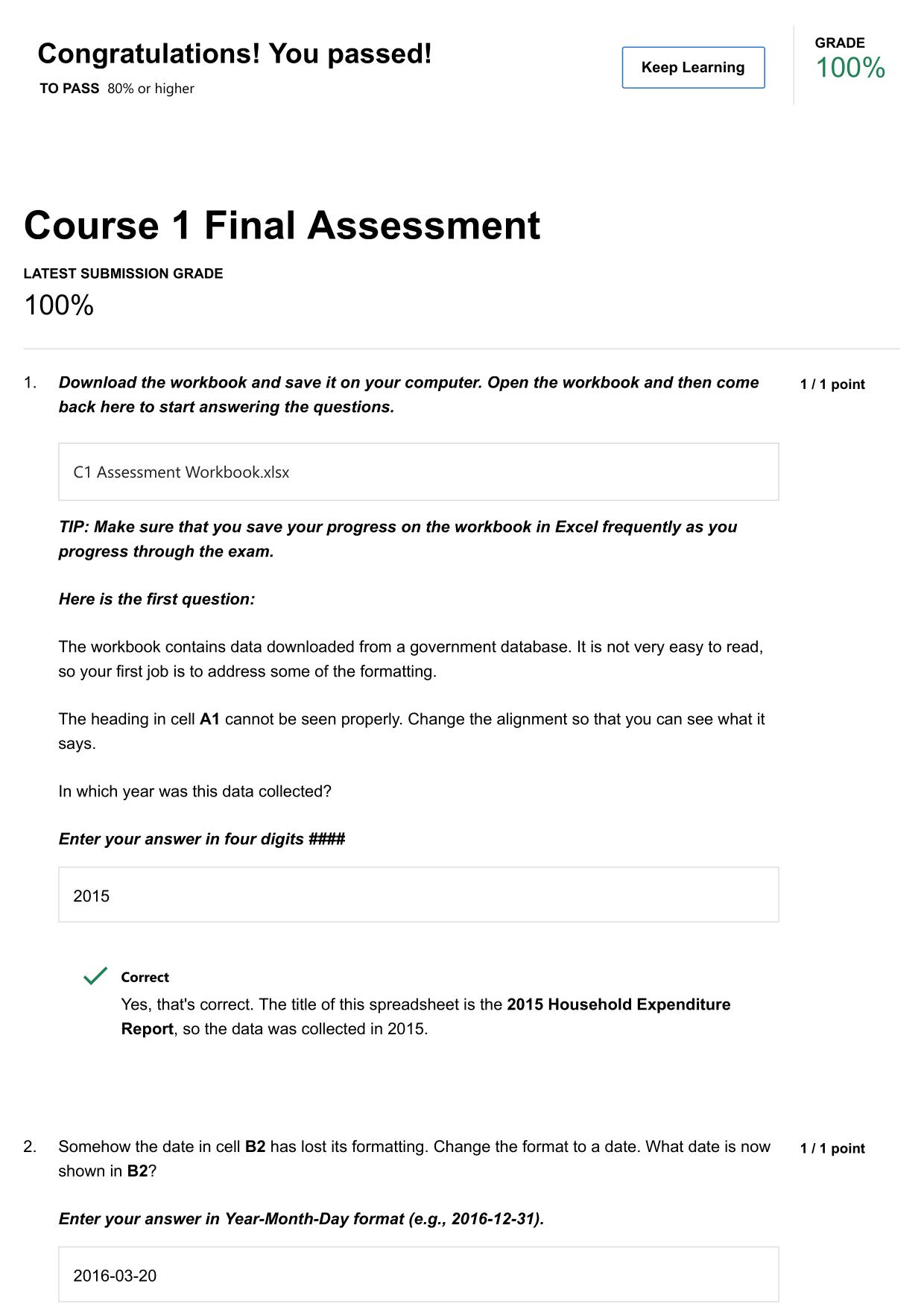
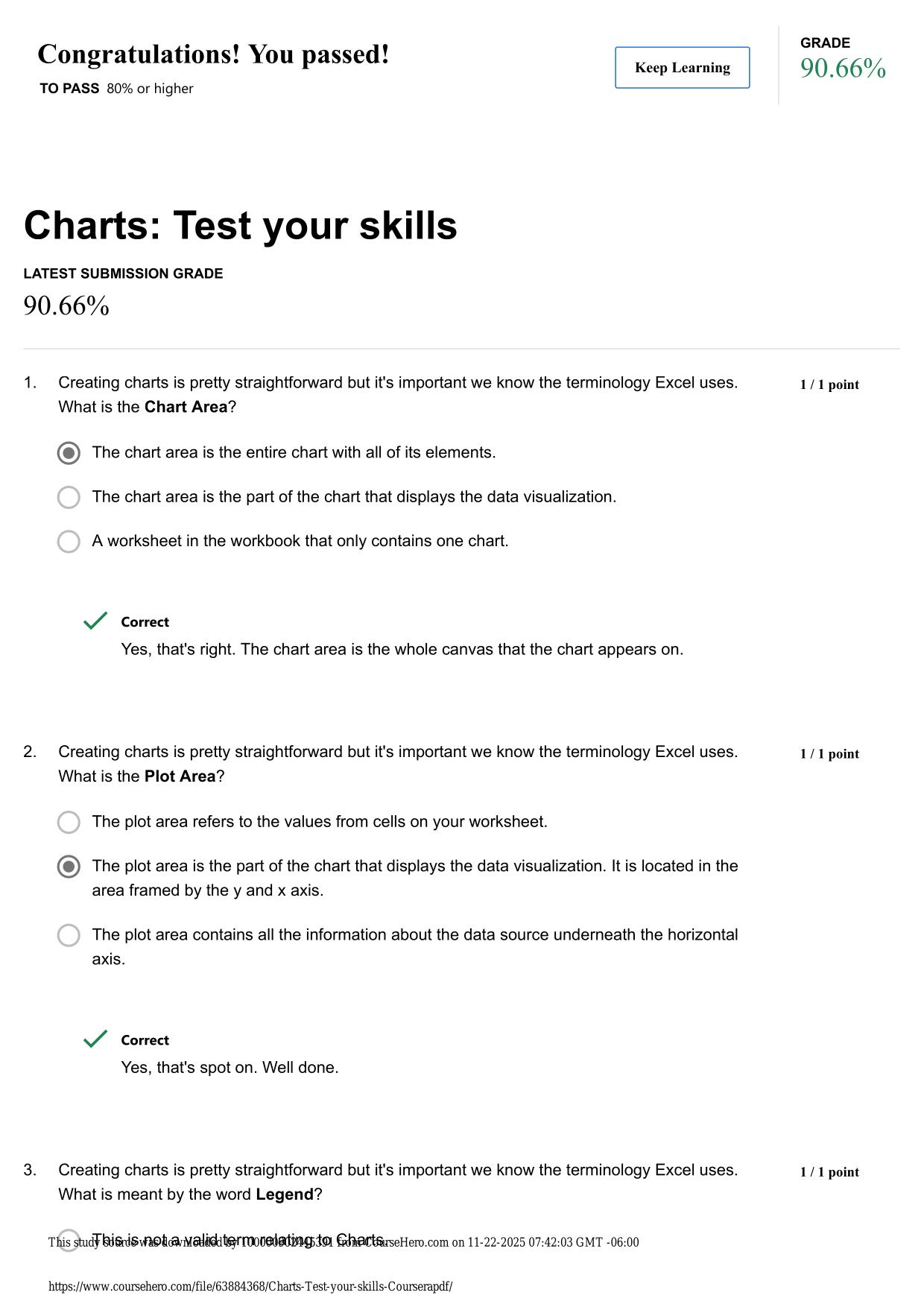
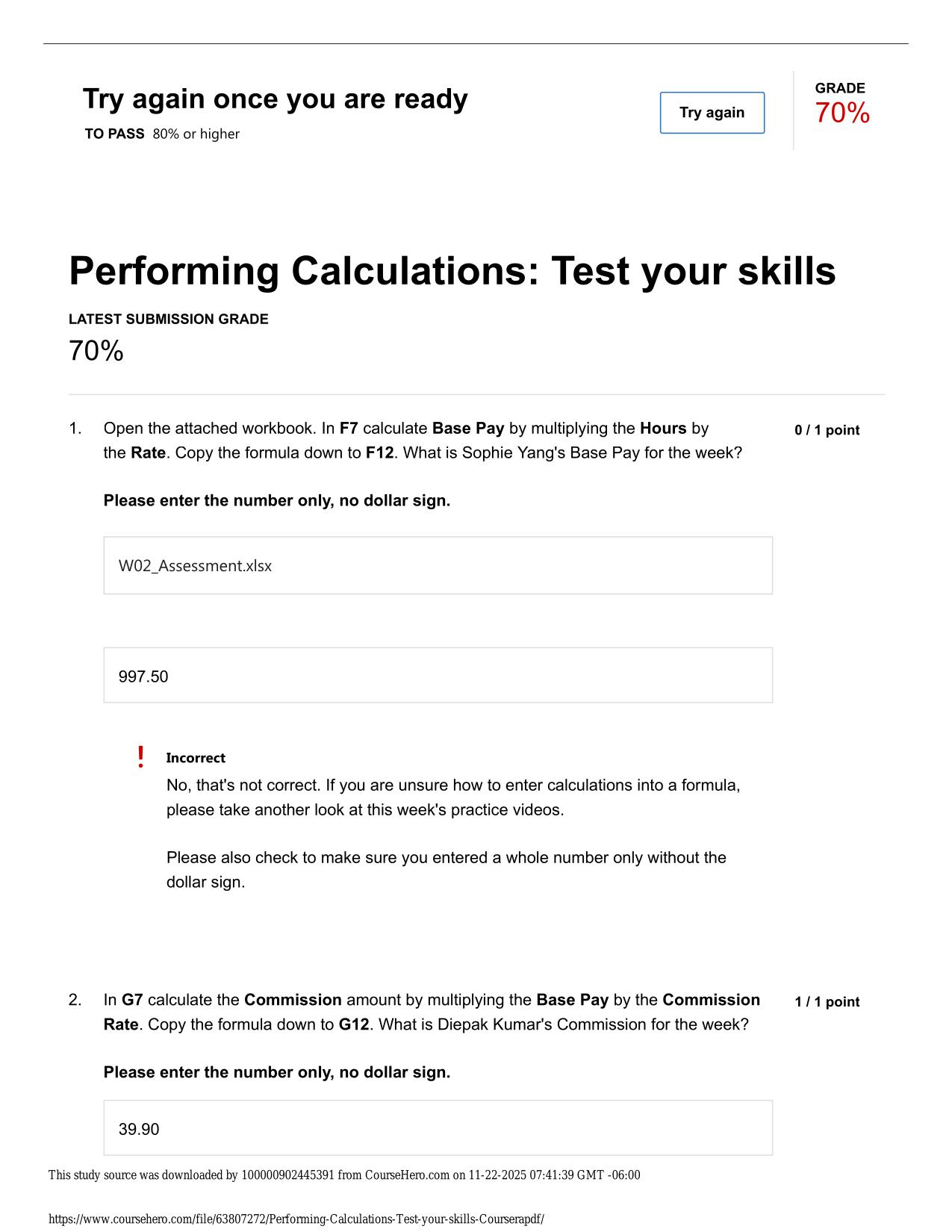
FY24 CYBER AWARENESS CHALLENGE ACTUAL 2025/2026 QUESTIONS AND 100% CORRECT ANSWERS Which of the following is true of working with a Sensitive Compartmented Information Facility (SCIF)? - Answer -Authorized personnel who permit another individual to e...
After purchase, you get:
✅ Instant PDF Download
✅ Verified answer explanations
✅ Refund if not Satisfied
✅ Prepared for 2025/2026 test cycle
Overview
This section strengthens analytical skills, helping users understand how exam questions are methodical and graded. You'll develop insight into what examiners are looking for in complete, well-reasoned answers. This understanding helps you tailor your responses to meet scoring criteria more effectively. Many test-takers find this strategic awareness gives them an edge in maximizing their points on complex items.
Who Is This For?
Created for exam takers seeking maximum exposure to typical Exam (elaborations) questions, rationales, and scenarios. People often use it to test their readiness before the actual exam. The all-inclusive coverage ensures thorough preparation.
Related Keywords
Detailed Study Description
Frequently Asked Questions
Document Information
| Uploaded on: | October 31, 2025 |
| Last updated: | November 17, 2025 |
| Number of pages: | 13 |
| Written in: | 2025/2026 |
| Type: | Exam (elaborations) |
| Contains: | Questions & Answers |
| Tags: | FY24 CYBER AWARENESS CHALLENGE ACTUAL 2025/2026 QUESTIONS AND 100% CORRECT ANSWERS Which of the following is true of working with a Sensitive Compartmented Information Facility (SCIF)? - Answer -Authorized personnel who permit another individual to enter the SCIF are responsible for confirming the individual's need-to-know and access. Which of the following is NOT a best practice for travelling overseas with a mobile device? - Answer -Store the device in a h |
Seller Information

AdelineJean
User Reviews (0)
Exam (Elaborations)
$7.50
Bundle Deal! Get all 6 docs for just $18.00
Add to Cart
100% satisfaction guarantee
Refund Upon dissatisfaction
Immediately available after purchase
Available in Both online and PDF
$7.50
| 0 sold
Discover More resources
Available in a Bundle
Inside The Document
FY24 CYBER AWARENESS CHALLENGE ACTUAL 2025/2026 QUESTIONS AND 100% CORRECT ANSWERS Which of the following is true of working with a Sensitive Compartmented Information Facility (SCIF)? - Answer -Authorized personnel who permit another individual to enter the SCIF are responsible for confirming the individual's need-to-know and access. Which of the following is NOT a best practice for travelling overseas with a mobile device? - Answer -Store the device in a hotel safe when sightseeing How should government owned removable media be stored? - Answer -In a GSA-approved container according to the appropriate security classification Which of the following is NOT a way that malicious code can spread? - Answer -Running a virus scan How can you protect your home computer? - Answer -Turn on the password feature, regularly back up your files Carl receives an e-mail about a potential health risk caused by a common ingredient in processed food. Which of the following actions should Carl NOT take with the e-mail? - Answer -Forward it Which of the following is an appropriate use of a DoD Public Key Infrastructure (PKI) token? - Answer -Do not use a token approved for NIPRNet on SIPRNet Which of the following is NOT a best practice for protecting data on a Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com mobile device? - Answer -Disable automatic screen locking after a period of inactivity Under which Cyberspace Protection Condition (CPCON) is the priority focus limited to critical and essential functions? - Answer -CPCON 2 When is the safest time to post on social media about your vacation plans? - Answer -After the trip Which of the following statements about Protected Health Information (PHI) is false? - Answer - You receive a phone call offering you a $50 gift card if you participate in a survey. Which course of action should you take? - Answer -Decline to participate in the survey. This may be a social engineering attempt. Tom is working on a report that contains employees' names, home addresses, and salary. Which of the following is Tom prohibited from doing with the report? - Answer -E-mailing it to a colleague who needs to provide missing data How can you protect your home computer? - Answer -Regularly back up your files Which of the following is a best practice to protect your identity? - Answer -Order a credit report annually. Annabeth becomes aware that a conversation with a co-worker that involved Sensitive Compartmented Information (SCI) may have been overheard by someone who does not have the required clearance. What action should Annabeth take? - Answer - Sylvia commutes to work via public transportation. She often uses the time to get a head start on work by making phone calls or responding to e-mails on her government approved mobile device. Does this pose a Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com
CourseHero & Studypool Unlocks
Get Unlocked CourseHero and Studypool documents files instantly to your email, simply by pasting your link and clicking "Unlock Now". Learn more on how to unlock here.